Cloud Security 1.0 Exam Braindumps
Killexams.com 850-001 Exam Braindumps contain complete question pool, updated in April 2024 including VCE exam simulator that will help you get high marks in the exam. All these 850-001 exam questions are verified by killexams certified professionals and backed by 100% money back guarantee.
850-001 resources - Cloud Security 1.0 Updated: 2024 | ||||||||
| Simply retain these 850-001 dumps questions before you go for test. | ||||||||
 |
||||||||
|
||||||||
|
Exam Code: 850-001 Cloud Security 1.0 resources January 2024 by Killexams.com team | ||||||||
850-001 Cloud Security 1.0 Exam Detail: The exam with the code 850-001, also known as "Cloud Security 1.0," is designed to evaluate the knowledge and skills of individuals in cloud security principles, best practices, and technologies. Here is a detailed overview of the exam, including the number of questions and time, course outline, exam objectives, and exam syllabus. Number of Questions and Time: The exact number of questions in the 850-001 exam may vary, but it typically consists of approximately 40 to 60 multiple-choice and scenario-based questions. The duration of the exam is usually around 90 minutes. Course Outline: The 850-001 certification exam covers various courses related to cloud security, including principles, technologies, and best practices. The specific course outline may include the following components: 1. Cloud Security Fundamentals: - Introduction to cloud computing and its security challenges - Cloud service models (IaaS, PaaS, SaaS) and deployment models (public, private, hybrid) - Cloud security roles and responsibilities - Legal and regulatory considerations in cloud security 2. Cloud Security Architecture: - Cloud security controls and frameworks - Secure cloud network design and architecture - Identity and access management in the cloud - Data protection and encryption in the cloud - Virtualization security 3. Cloud Security Technologies: - Cloud provider security tools and services - Intrusion detection and prevention systems (IDPS) in the cloud - Security information and event management (SIEM) in the cloud - Vulnerability assessment and penetration testing in the cloud - Incident response and forensics in the cloud 4. Cloud Security Best Practices: - Secure cloud application development and deployment - Secure configuration and patch management in the cloud - Cloud security monitoring and auditing - Security considerations for cloud data storage and backup - Disaster recovery and business continuity planning in the cloud Exam Objectives: The objectives of the 850-001 certification exam are to assess the candidate's understanding and proficiency in various aspects of cloud security. The specific objectives include: - Knowledge of cloud computing concepts and models - Understanding of cloud security risks and challenges - Familiarity with cloud security controls and best practices - Proficiency in designing and implementing secure cloud architectures - Knowledge of cloud security technologies and tools - Understanding of legal and regulatory considerations in cloud security - Ability to perform cloud security monitoring and incident response Exam Syllabus: The 850-001 exam syllabus outlines the specific courses and subtopics that will be covered in the exam. The syllabus may include: - Introduction to cloud computing and security challenges - Cloud service models and deployment models - Cloud security roles and responsibilities - Legal and regulatory considerations in cloud security - Cloud security controls and frameworks - Secure cloud network design and architecture - Identity and access management in the cloud - Data protection and encryption in the cloud - Virtualization security - Cloud provider security tools and services - Intrusion detection and prevention systems (IDPS) in the cloud - Security information and event management (SIEM) in the cloud - Vulnerability assessment and penetration testing in the cloud - Incident response and forensics in the cloud - Cloud application security best practices - Secure configuration and patch management in the cloud - Cloud security monitoring and auditing - Security considerations for cloud data storage and backup - Disaster recovery and business continuity planning in the cloud | ||||||||
| Cloud Security 1.0 Symantec Security resources | ||||||||
Other Symantec exams250-251 Administration of HA Solutions for UNIX (VCS 5.0)250-351 Administration of HA Solutions for Windows using VCS 5.0 250-406 Administration of Clearwell eDiscovery Platform 7.x 250-407 Prepare for Symantec Symantec Client Management Suite 7.x 850-001 Cloud Security 1.0 250-428 Administration of Symantec Endpoint Protection 14 250-561 Endpoint Security Complete ? Administration R1 250-556 Administration of Symantec ProxySG 6.7 | ||||||||
| killexams.com 850-001 Certification dumps are Verified by our certified experts. All the error are removed from 850-001 brain dumps. VCE exam simulator is carefully build so that you can consume maximum 850-001 exam knowledge. You just need to memorize our 850-001 dumps, Braindumps and practice with VCE exam simulator to get full marks in the exam. | ||||||||
| Symantec 850-001 Cloud Security 1.0 https://killexams.com/pass4sure/exam-detail/850-001 Question: 90 Which action addresses a risk inherent to the public cloud model? A. harden applications sufficiently for multi-tenant environments B. revert a public cloud to a private cloud during an emergency C. apply anti-spam measures on the endpoint accessing the cloud D. activate deduplication on the cloud-based storage Answer: A Question: 91 In order to achieve greater scalability, a CIO has mandated that a specific set of processes and data move to a cloud environment. These assets include: – Company email requiring anti-spam protection – Proprietary database with specific infrastructure requirements – Point-of-sale application and process for retail purchases. Which service and deployment model could support all of these assets? A. Infrastructure as a Service, hosted in a private cloud B. Platform as a Service, hosted in a public cloud C. Software as a Service, hosted in a private cloud D. Software as a Service, hosted in a public cloud Answer: A Question: 92 A company is moving to the cloud. Because of DDOS attacks, it would like to start by moving email to the cloud. The company is small, with fewer than 200 users. What is the most cost- effective deployment model for this company to begin using? A. IaaS community B. IaaS public C. PaaS hybrid D. SaaS public Answer: C Question: 93 Several government agencies collaborate extensively, sharing a variety of tools, processes, and data. Data shared by the organizations is highly sensitive, and risk tolerance for data loss or exposure is extremely low. Which type of cloud solution is appropriate in this scenario? A. internally-hosted infrastructure providing a community cloud B. internally-hosted infrastructure providing a private cloud C. externally-hosted infrastructure providing a community cloud D. externally-hosted infrastructure providing a private cloud Answer: A Question: 94 A large enterprise that is currently supported by a very large IT infrastructure and experienced staff would like to offer individual Business Units (BUs) the ability to use local servers and storage on an as-needed basis. The BUs would then be charged accordingly, based on their individual usage. Which cloud service and deployment model combination provides an appropriate solution? A. Platform as a Service, public cloud B. Platform as a Service, private cloud C. Infrastructure as a Service, public cloud D. Infrastructure as a Service, private cloud Answer: D Question: 95 A current customer’s cloud service provider is undergoing a merger and acquisition process. This increases the likelihood of a strategic shift to the customer’s business operations and may put non-binding agreements at risk, as well as make compliance with security requirements impossible. How is this cloud provider acquisition risk categorized? A. policy and organizational B. technical C. lock-in D. non-cloud specific Answer: A Question: 96 A cloud service provider administrator has discovered that someone is attempting to determine which servers and operating systems are running on a tenant’s network by using network mapping. How is this risk categorized? A. policy and organizational B. technical C. legal D. non-cloud specific Answer: B Question: 97 A cloud customer has determined that their data is being held in multiple geographic locations. They are concerned that these sites will be raided by local authorities and their data or systems are subject to disclosure or seizure. Which risk category does this type of risk fall into? A. policy and organizational B. technical C. legal D. non-cloud specific Answer: C Question: 98 An IT security professional at a large US-based manufacturing company has decided to deploy and manage a host intrusion detection solution to assist with their migration to a cloud environment. Which cloud environment will benefit from this solution? A. multi-tenant SaaS B. hybrid SaaS C. multi-tenant IaaS D. multi-tenant PaaS Answer: C Question: 99 Which action addresses a risk inherent to the public cloud model? A. harden applications sufficiently for multi-tenant environments B. revert a public cloud to a private cloud during an emergency C. apply anti-spam measures on the endpoint accessing the cloud D. activate deduplication on the cloud-based storage Answer: A Question: 100 A company has decided to implement "cloud bursting" to allow their production environment to scale to any size by utilizing on-demand connections to a public cloud IaaS infrastructure. Which solution allows the IT department to protect against VM hopping? A. data loss prevention B. anti-virus / anti-spam C. data and mail encryption D. host intrusion prevention Answer: A For More exams visit https://killexams.com/vendors-exam-list Kill your exam at First Attempt....Guaranteed! | ||||||||
|
Symantec has purchased Appthority and Javelin Networks to strengthen its defense against mobile application attacks and boost its protection around Microsoft Active Directory-based threats. The Mountain View, Calif.-based platform security vendor said the acquisitions of San Francisco-based Appthority and Austin, Texas-based Javelin Networks will further enhance Symantec's ability to protect the broadest spectrum of modern endpoints and operating systems. Appthority will make it possible for Symantec customers to analyze mobile applications for both malicious capabilities as well as unsafe or unwanted behaviors such as vulnerabilities, risk of sensitive data loss, or privacy-invasive actions. The company was founded in 2011, employs 35 people, and has raised $25.3 million in four rounds of outside funding, according to LinkedIn and Crunchbase. [Related: Symantec CEO: Our Endpoint Security Is More Effective Than Our Peers] The company's technology will be built into Symantec Endpoint Protection Mobile, making Symantec the only company to protect modern and traditional Windows, MacOS, Linux, iOS, and Android endpoints at the device, application, network, identity and cloud layers. Buying Appthority will help Symantec combine mobile app analysis and mobile threat defense to enhance overall security and workflow. "Mobile apps are a critical threat vector that every company must address to protect their enterprise security," Adi Sharabani, Symantec SVP, Modern OS Security, said in a statement. "The Appthority technology extends SEP (Symantec Endpoint Protection) Mobile's capabilities in limiting unwanted app behaviors, supporting regulatory compliance, and assessing vulnerabilities." Javelin Networks, meanwhile, can detect Active Directory misconfigurations and backdoors, and help prevent Active Directory reconnaissance and credentials misuse by authorized devices and applications. The company was founded in 2014, employs 21 people, and has raised $5 million in two rounds of outside funding, according to LinkedIn and Crunchbase. Active Directory services have become an increasingly popular target for attackers, who use the reconnaissance features to discover the users, servers and computers in an enterprise network and then move laterally across the network. Javelin Networks' software protect Active Directory and commonly-used domain resources, including domain controllers, domain identities, and domain credentials. "The addition of Javelin Networks … gives Symantec customers a unique advantage in one of the most vulnerable and critical areas of IT infrastructure," Javed Hasan, Symantec's SVP of endpoint and data center products, said in a statement. "More importantly, it can help expose exploitable backdoors in AD (Active Directory) and stop attacks at the point of breach while preventing lateral movement." Symantec's stock is up 2.05 percent to $19.90 in trading Monday morning. Terms of the transactions were not disclosed, and Symantec did not immediately respond to a request for additional comment. This is Symantec's first acquisition since buying VPN browser security application SurfEasy in November 2017. Symantec carried out five transactions in 2017 – highlighted by its $250 million purchase of agentless isolation provider Fireglass - but failed to make a single acquisition in the first 10 months of 2018. Symantec must focus on fully integrating the Appthority and Javelin Networks capabilities into the company's existing cloud management platform, according to Marc Harrison, president of Marlboro, N.J.-based solution provider Silicon East. Doing this successfully will make it possible for channel partners to manage the entire Symantec security suite from a single interface.
Symantec has purchased Luminate Security to better protect users around workloads and applications regardless of where they're deployed or what infrastructure they're accessed through. The Mountain View, Calif.-based platform security vendor said its acquisition of Palo Alto, Calif.-based cybersecurity startup Luminate Security will make it possible to deliver private secure application access, granting user connections only to the specific applications and resources for which they are authorized. More and more companies are operating their business on infrastructure that is managed by multiple third parties such as Azure, AWS and Google, according to Symantec President and CEO Greg Clark. Secure and private access are a cornerstone of cyber defense, said Clark, who is looking forward to delivering Luminate's unique capabilities to customers. [Related: Duo Sales Leader Departs For Startup Following Cisco Acquisition Bid] "In this rapidly evolving world, trust in external infrastructure must be carefully considered as corporations can outsource infrastructure but must also remain responsible for data and users," Clark said in a statement. "Luminate incorporated into Symantec's Integrated Cyber Defense puts us at the forefront of security in the cloud era." Symantec said its Integrated Cyber Defense Platform unifies cloud and on-premises security across endpoints, networks, email and cloud, protecting against the most sophisticated threats while reducing cost and complexity. This allows companies and users to have frictionless access to cloud and on-premises applications while still providing best-of-breed security protection, according to Symantec. "As corporate applications continue to move to the cloud, IT organizations need innovative approaches to address the complexity and security challenges of providing users anywhere, anytime access," Art Gilliland, Symantec's EVP and GM of enterprise products, said in a statement. Terms of the deal were not disclosed. Symantec's stock was up nearly 3 percent to $23.09 in trading Wednesday morning. Luminate Security was founded in 2017, employs 39 people, and has raised $14 million in two rounds of outside funding, according to LinkedIn and Crunchbase. The company in August reeled in Duo Security sales leader Jason Stutt to serve as its first-ever senior vice president of global sales and help Luminate scale its operations in North America. "As a partner, our integrations with Symantec were successful in reducing complexity and increasing security for joint customers," Ofer Smadari, Luminate Security CEO, said in a statement. "With this next step, we look forward to fully integrating across the entire portfolio and delivering even more innovation to offer complete security for the Cloud Generation." Luminate Security emerged from stealth in March 2018 with a Series A funding led by U.S. Venture Partners to expand its operations in the United States and develop its channels and customer base. In April 2018, Luminate announced general availability of its platform, which provides secure access to corporate applications in hybrid cloud environments. The Luminate platform provides employees with a consistent, cloud-native experience around any corporate application regardless of where it's hosted, the device being used, or where the worker is located. All user activities are examined against company policies, triggering automatic actions to ensure security is being enforced and to prevent unauthorized access. Symantec has made 72 acquisitions over its 37-year history, according to Crunchbase. The company's most recent acquisitions were of Appthority and Javelin Networks in November 2018 to strengthen the company's defense against mobile application attacks and boost its protection around Microsoft Active Directory-based threats. One Luminate Security partner who didn't wish to be identified said the deal will provide Symantec with a very clear and unique offering, but will challenge the Luminate team to maintain its mindset, energy and capabilities within a much larger company. "It is a challenging process to integrate and merge into a very big company," the partner said. "But it doesn’t mean it's impossible." The partner encouraged Symantec to keep Luminate as a standalone operation and maintain the company's product and brand. If the acquisition preserves Luminate's expertise and create opportunities for solution providers to cross-sell the Luminate offering into Symantec's legacy customer base, it'll be a win-win for the channel, according to the partner. "Don't mix Luminate with the bigger company. Keep them small and with their familiar development team," the partner said. "Just let them work as they are." At Symantec, we believe Cyber Resilience is about the management--not the elimination--of risk. We recognise that security needs to go beyond systems, software or IT departments. Cyber Resilience puts the power in the hands of people, and arms them with the ability to recognise risks, draw on the collective intelligence of others, and take preventive or corrective action. We believe Cyber Resilience calls for strategic action. Now. To help achieve this we propose a new strategic partnership between the security function and business leaders, to balance competitive advantage against the inescapable Cyber Risk of today. Our integrated portfolio of solutions helps your people:
It is time to raise the stakes. University of Nevada, Reno information security policies and procedures Security awareness training: Faculty and staff have free information security awareness training available to them. Some of the courses covered in this general security awareness course include: privacy, threats, safe computing best practices, password best practices, malware, social engineering, phishing, physical security, data security, and mobile and remote computing best practices. In addition to the free managed training available to all faculty and staff, employees can also take advantage of security awareness training through Lynda.com. Within our internal SharePoint compliance site, users are given resources to the recommended Lynda.com courses. Online security resourcesJoin leaders in San Francisco on January 10 for an exclusive night of networking, insights, and conversation. Request an invite here. All it takes is a single hijacked browser session or unprotected third-party device on a network to shut a business down, costing millions in lost productivity and revenue. Regarding browser attacks, many CISOs can’t forget how the CNA Financial breach started with a phishing email telling an admin to perform a browser update. Attackers infiltrated the CNA network, infecting 15,000 systems with ransomware while destroying backups and disabling monitoring and security tools. The growing risk of unmanaged endpoints Enterprises are overwhelmed with more work than their teams can handle. Department leaders turn to contractors to complete more work and expect employees to be available on any web-enabled device. Organizations find hundreds of new unmanaged endpoints on their networks, with every contractor and employee relying on their laptops, tablets and phones to get work done. Asking every contractor to load a series of special software or applications on their devices isn’t practical and gets limited adoption. It also burdens already stretched IT staff, who are called on to help. The paradox gets more challenging when organizations need contractor help to get up and running fast to keep up with workloads yet need a security solution that scales across thousands of device types. VB EventThe AI Impact Tour Getting to an AI Governance Blueprint – Request an invite for the Jan 10 event. Onboarding contractors quickly sometimes leads to as many as 40% of new endpoints needing to be traced or even discoverable on the network. When a contractor is onboarded, they often get access to shared productivity apps. As many organizations don’t have a process to delete a contractor’s access by cloud app or resource, credentials can live on for years – even decades – and lead to intrusion and breach attempts.  Identifying the new wave of web-based attacks Fake browser update scams are on the rise today. These attacks rely on websites that tell users to update their browsers to see the content. Brian Krebs, a cybersecurity investigative reporter and blogger, writes, “New research shows the attackers behind one such scheme have developed an ingenious way of keeping their malware from being taken down by security experts or law enforcement: By hosting the malicious files on a decentralized, anonymous cryptocurrency blockchain.” Earlier this year, security researcher Randy McEoin discovered and wrote about a web browser attack strategy he called ClearFake. The attack strategy starts with WordPress sites that provide victims with a webpage that tells the user to update their browser before they can view the content. Sekoia.io’s Quentin Bourgue and the Threat & Detection Research Team provide a comprehensive technical analysis of how ClearFake works and insights into its installation flow.  Source: Sekoia blog Start by securing unmanaged endpoints at the browserÂCISOs are challenged with managing hundreds or thousands of endpoints that often change as contractors are onboarded or let go when their contracts expire. IT and security teams rely on web application isolation because it’s been proven to protect from web-based threats that target an organization’s most valuable apps and resources. Leading cybersecurity vendors who provide web application integration solutions include Broadcom/Symantec, Cloudflare, Cradlepoint, Forcepoint, Iboss, Menlo Security, McAfee, NetSkope and Zscaler. The technology behind web application isolation is the same for remote browser isolation (RBI), only used in reverse. Instead of preventing hackers from targeting and breaching a network through endpoint web browsers, it prevents hackers from being able to target and breach corporate web or cloud applications. Cradlepoint is differentiated in its support and delivery of comprehensive, two-way protection for the application and its users. How remote browser isolation worksRBI uses a zero-trust approach to secure every endpoint and the apps and resources it has access to, treating all active code from a website as a threat, whether malicious or not. It takes a zero-trust approach to protect any device from the latest, unknown web-based threats. Zero-day threats can often evade detection by traditional solutions, such as antivirus solutions, which rely on a database of known signatures to detect threats. Since zero-days are, by definition, unknown, traditional solutions cannot detect them. RBI assumes that all websites may contain malicious code and isolates all content from endpoints to prevent malware, ransomware and malicious scripts or code from impacting an organization’s systems. All sessions are run in a secure, isolated cloud environment, enforcing least-privilege application access at the browser session-level. Like RBI, a web application isolation solution doesn’t affect the user experience. The secure web application is still completely functional and interactive. Behind the scenes, web isolation technology is keeping the application secure. Like a web application firewall (WAF), RBI protects applications from Layer 7 attacks. RBI differs from WAF because it isn’t designed to deliver zero trust security to every browser session. WAFs have signatures that can catch threats, but zero-day attacks have been known to breach them. Combining authorization and isolation technologies blocks attackers from breaching applications and embedding malicious code. That’s essential for protecting end-users from phishing attempts, malware infections and other application-based attacks. The goal is to protect internal systems, networks and data accessible or linked to applications that risk being compromised. Relying on the OWASP Top 10 framework is table stakes for designing an RBI architecture resilient to risks.  Of the RBI solutions available, Cradlepoint’s Ericom is differentiated in its combining a secure web gateway (SWG) with built-in remote browser isolation (RBI) to provide zero-trust security for web browsing. Security teams use web application isolation to apply granular user-level policies to control which apps every user can access, regardless of location and role. Those granular controls define which actions they can complete in each app. It’s common for (WAI) platforms to support policies controlling file upload/download permissions, malware scanning, DLP scanning, and limit cut-and-paste functions (clip-boarding) and users’ ability to enter data into text fields. The solution also “masks” the application’s attack surfaces from would-be attackers, protecting against the OWASP Top 10 Web Application Security Risks. Cradlepoint’s Ericom bases web application isolation (WAI) on their remote browser isolation (RBI) expertise and years of helping SMBs with zero-trust initiatives and frameworks. Source: Ericom Getting it doneÂRemote work and the widespread use of personal devices create entirely new threat surfaces that organizations aren’t staffed or funded with enough budget to provide endpoint software agents. That’s why browser-based approaches are catching on. The following are table stakes for securing unmanaged devices in today’s zero-trust world: Identification and Categorization of Assets: Begin by thoroughly identifying all enterprise applications, data, and resources. Categorize them based on their sensitivity and the level of access required. Deployment of Web Application Isolation Techniques: To combat the risk of unmanaged devices causing a breach, get familiar with web application isolation techniques. Even if an attacker reaches the device, installing web application isolation will protect applications. Enforcing Least Privilege Access: First, audit and then identify what resources each role or identity needs and restrict access to other apps, resources, or databases. This alone can reduce the potential for an insider threat and reduce any accidental access to sensitive data. Continuous Monitoring and Adaptive Policies: A core concept of zero trust is monitoring every resource request and transaction over a network. Getting this right provides the data to identify threats and track breach attempts. Multi-Factor Authentication (MFA): This needs to be table stakes for every contractor and employee on the network using any app or resource. Require it for access to the network and also for any app, database or collaborative app.  Encrypt Sensitive Data: Ensure that all sensitive data, both at rest and in transit, is encrypted. This protects data integrity and confidentiality, even if attackers gain access. Data Loss Prevention (DLP): Essential for enforcing safeguards against exposure of confidential and personally identifiable information (PII), data loss prevention (DLP) is essential for an organization to have a hardened security posture. It’s increasingly considered core to zero-trust security frameworks.  Segment Networks: Getting network segmentation right is worth it. Shutting down the lateral movement of attackers by segmenting the network pays dividends the first time an intrusion attempt goes nowhere. Implement Endpoint Security Solutions: Use advanced endpoint security tools to monitor and manage devices accessing the network. This includes ensuring that all devices are updated with the latest security patches. Regular Security Training and Awareness Programs: Training can help raise awareness of the most blatant phishing attempts, malicious links, and other common threats. See it as a support strategy, not the core of any cybersecurity program.  Get vendors and partners onboard early: Extend RBI to third-party vendors and partners immediately to protect supply chains and partner networks. Ensure they adhere to similar security standards to protect shared networks and data. These are just a start to getting unmanaged devices secured. Using these suggestions as a baseline to get started will help reduce the risk of a breach starting on a third-party device. Having RBI running when there’s a large influx of contractors globally working on projects is essential for protecting infrastructure. VentureBeat's mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Discover our Briefings. Anti-virus software works by comparing the files on your computers and those you access online to a database of known viruses, known as virus definitions. Without regularly updated definitions, an anti-virus program won't protect your computers and office workstations against new viruses. All paid anti-virus programs, including Symantec's Norton AntiVirus and their business editions, sell definition updates through subscription plans, and no longer update the definitions once the subscription expires. Unlike some other brands however, current versions of Symantec's programs will completely stop functioning -- even with old definitions -- after the subscription ends, leaving the computers on your network unprotected. Smart, connected production machinery has transformed manufacturing, leading to tremendous productivity, safety and quality gains. However, the Industrial Internet of Things (IIoT) has also created new security risks. Connected machines represent a cybersecurity endpoint in the smart factory that can put facilities and data at risk. Strong endpoint security practices—including machine user authentication—are needed to protect valuable intellectual property (IP), prevent production delays, and ensure the safety of people and facilities. Cyberattacks on manufacturers are rising, with an average cost of $4.47 million per incident in 2022. Many of these are traditional attacks on IT infrastructure, such as phishing attacks, ransomware and malware attacks on websites or networks. However, as manufacturers ramp up their use of IIoT and operational technology (OT) devices, production machinery has become a tempting target for hackers and bad actors. Attacks on production machinery or safety-instrumented systems (SIS) can cause considerable operational disruption. IIoT and OT devices are cyber-physical systems that act as endpoint devices for the factory network. In addition to risks presented by unauthorized access to machine controls and software, they also increase the attack surface for the factory as a whole, allowing bad actors to use them as a pivot point into other IT systems. Unprotected IIoT devices leave factories vulnerable to data breaches, malware and ransomware attacks, denial of service attacks, and other potential harms. Cyberattacks on production machinery can cause severe damage, including:
In many factories, production machines are among the most vulnerable network endpoints. This is partly because IT and OT tend to exist in silos, with IT handling traditional endpoint devices (laptops, printers, servers, etc.), while the operations department handles machinery on the factory floor. The 2019 Deloitte and MAPI Smart Factory Study suggests that IT and OT are seriously misaligned in many factories, leading to significant vulnerabilities on the factory floor. Other factors that increase cyber risk include:

To protect people, data, and production machinery, manufacturers need a comprehensive cybersecurity strategy. Photo courtesy ELATEC Inc. Best Practices in OT and IIoT CybersecurityTo protect people, data, and production machinery, manufacturers need a comprehensive cybersecurity strategy. This requires adopting best practices and complying with industry standards and regulations. One of the most essential things manufacturers can do is break down the silos between OT and IT. When considering production machinery as a network endpoint, it becomes clear that OT and IIoT devices must have the same level of attention and protection as laptops, servers and other IT devices. That means adopting best practices from the IT side. These measures include:
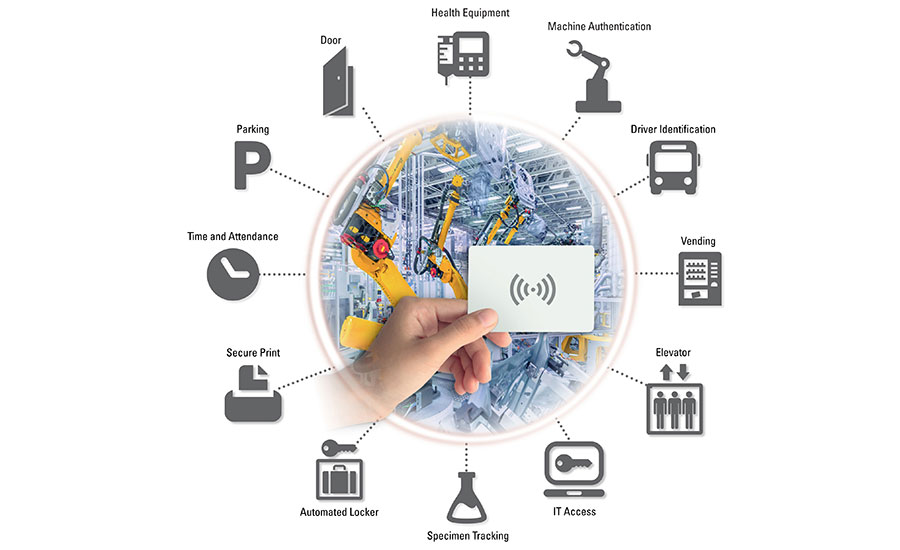
With RFID, the same access control technology can be used for physical access control, machine authentication, and digital access to systems and networks. Photo courtesy ELATEC Inc. Protect Production Machinery With Strong User AuthenticationMachine authentication is a cornerstone of endpoint security in the smart factory. Strong authentication technology ensures that only authorized, trained operators can access controls for production machinery and allows companies to track exactly who has accessed each machine and at what times. The right machine authentication solution can also reduce the risk of remote hacking. Many manufacturers still rely on password or PIN systems for machine access. However, passwords and PINs are often shared or forgotten. They can also be hacked. Radio-frequency identification (RFID) offers a more secure alternative to a password or PIN for machine authentication. Users present a physical badge or token to unlock access to the machine. This can also be accomplished via a mobile credential on a smartphone using near-field communication (NFC) or Bluetooth low energy (BLE). An RFID or mobile solution for machine authentication increases machine security in several ways. First, these systems are highly secure and difficult to clone or hack when appropriate encryption is used. Physical badges, tokens or phones are also less likely to be shared than a password or PIN. In addition, the user must be physically present at the machine with the badge, token or device in hand to unlock access, reducing the risk that the machine can be inappropriately accessed via remote hacking or password theft. For higher security, RFID and mobile access solutions can be implemented as part of a multifactor authentication process using a secondary password or biometric system. Finally, loss or theft of a physical badge, token or device is likely to be noticed immediately, unlike a compromised password. IT can quickly and easily shut off authorization if a card is lost or stolen or an employee leaves the company. 
Physical badges are also less likely to be shared than a password or PIN. In addition, the user must be physically present at the machine with the badge in hand to unlock access. Photo courtesy ELATEC Inc.
| ||||||||
850-001 learn | 850-001 health | 850-001 test prep | 850-001 study tips | 850-001 mission | 850-001 Questions and Answers | 850-001 education | 850-001 pdf | 850-001 approach | 850-001 teaching | | ||||||||
Killexams exam Simulator Killexams Questions and Answers Killexams Exams List Search Exams |