Configuring and Operating Windows Virtual Desktop on Microsoft Azure Exam Braindumps
Killexams.com AZ-140 Exam Braindumps contain complete question pool, updated in April 2024 including VCE exam simulator that will help you get high marks in the exam. All these AZ-140 exam questions are verified by killexams certified professionals and backed by 100% money back guarantee.
AZ-140 course outline - Configuring and Operating Windows Virtual Desktop on Microsoft Azure Updated: 2024 | ||||||||||
| Never miss these AZ-140 dumps questions before you go for test. | ||||||||||
 |
||||||||||
|
||||||||||
|
Exam Code: AZ-140 Configuring and Operating Windows Virtual Desktop on Microsoft Azure course outline January 2024 by Killexams.com team | ||||||||||
AZ-140 Configuring and Operating Windows Virtual Desktop on Microsoft Azure Exam Number: AZ-140 Exam Name : Configuring and Operating Windows Virtual Desktop on Microsoft Azure Exam TOPICS Exam AZ-140: Configuring and Operating Microsoft Azure Virtual Desktop Candidates for this exam are administrators with subject matter expertise in planning, delivering, and managing virtual desktop experiences and remote apps, for any device, on Azure. Responsibilities for this role include deploying virtual desktop experiences and apps to Azure. Professionals in this role deliver applications on Azure Virtual Desktop and optimize them to run in multi-session virtual environments. To deliver these experiences, they work closely with the Azure administrators and architects, along with Microsoft 365 Administrators. Candidates for this exam should have experience in Azure technologies, including virtualization, networking, identity, storage, backups, resilience, and disaster recovery. They should understand on-premises virtual desktop infrastructure technologies as they relate to migrating to Azure Virtual Desktop. These professionals use the Azure portal and Azure Resource Manager templates to accomplish many tasks. This role may use PowerShell and Azure Command-Line Interface (CLI) for more efficient automation. NOTE: The bullets that appear below each of the skills measured are intended to illustrate how we are assessing that skill. This list is NOT definitive or exhaustive. Plan an Azure Virtual Desktop Architecture (10-15%) Implement an Azure Virtual Desktop Infrastructure (25-30%) Manage Access and Security (10-15%) Manage User Environments and Apps (20-25%) Monitor and Maintain an Azure Virtual Desktop Infrastructure (20-25%) Plan an Azure Virtual Desktop Architecture (10-15%) Design the Azure Virtual Desktop architecture assess existing physical and virtual desktop environments assess network capacity and speed requirements for Azure Virtual Desktop recommend an operating system for an Azure Virtual Desktop implementation plan and configure name resolution for Active Directory (AD) and Azure Active Directory Domain Services (Azure AD DS) plan a host pools architecture recommend resource groups, subscriptions, and management groups configure a location for the Azure Virtual Desktop metadata calculate and recommend a configuration for performance requirements calculate and recommend a configuration for Azure Virtual Machine capacity requirements Design for user identities and profiles select an appropriate licensing model for Azure Virtual Desktop based on requirements recommend an appropriate storage solution (including Azure NetApp Files versus Azure Files) plan for Azure Virtual Desktop client deployment plan for user profiles recommend a solution for network connectivity plan for Azure AD Connect for user identities Implement an Azure Virtual Desktop Infrastructure (25-30%) Implement and manage networking for Azure Virtual Desktop implement Azure virtual network connectivity manage connectivity to the internet and on-premises networks implement and manage network security manage Azure Virtual Desktop session hosts by using Azure Bastion monitor and troubleshoot network connectivity Implement and manage storage for Azure Virtual Desktop configure storage for FSLogix components configure storage accounts configure disks create file shares Create and configure host pools and session hosts create a host pool by using the Azure portal automate creation of Azure Virtual Desktop host and host pools by using PowerShell, Command-Line Interface (CLI), and Azure Resource Manager templates create a host pool based on Windows client or Windows Server session hosts configure host pool settings manage licensing for session hosts that run Windows client or Windows Server assign users to host pools apply OS and application updates to a running Azure Virtual Desktop host apply security and compliance settings to session hosts Create and manage session host images create a gold image modify a session host image install language packs in Azure Virtual Desktop deploy a session host by using a custom image plan for image update and management create and use a Shared Image Gallery troubleshoot OS issues related to Azure Virtual Desktop Manage Access and Security (10-15%) Manage access plan and implement Azure roles and role-based access control (RBAC) for Azure Virtual Desktop manage local roles, groups and rights assignment on Azure Virtual Desktop session hosts configure user restrictions by using Azure AD group policies and AD policies Manage security plan and implement Conditional Access policies for connections to Azure Virtual Desktop plan and implement multifactor authentication in Azure Virtual Desktop manage security by using Azure Security Center configure Microsoft Defender Antivirus for session hosts Manage User Environments and Apps (20-25%) Implement and manage FSLogix plan for FSLogix install and configure FSLogix configure Profile Containers configure Cloud Cache migrate user profiles to FSLogix Configure user experience settings configure Universal Print configure user settings through group policies and Endpoint Manager policies configure persistent and non-persistent desktop environments configure Remote Desktop Protocol (RDP) properties on a host pool configure session timeout properties troubleshoot user profile issues troubleshoot Azure Virtual Desktop clients Install and configure apps on a session host configure dynamic application delivery by using MSIX App Attach implement application masking deploy an application as a RemoteApp implement and manage OneDrive for Business for a multi-session environment implement and manage Microsoft Teams AV Redirect implement and manage browsers and internet access for Azure Virtual Desktop sessions create and configure an application group troubleshoot application issues related to Azure Virtual Desktop Monitor and Maintain an Azure Virtual Desktop Infrastructure (20-25%) Plan and implement business continuity and disaster recovery plan and implement a disaster recovery plan for Azure Virtual Desktop design a backup strategy for Azure Virtual Desktop configure backup and restore for FSLogix user profiles, personal virtual desktop infrastructures (VDIs), and golden images Automate Azure Virtual Desktop management tasks configure automation for Azure Virtual Desktop automate management of host pools, session hosts, and user sessions by using PowerShell and Azure Command-Line Interface (CLI) implement autoscaling in host pools Monitor and manage performance and health monitor Azure Virtual Desktop by using Azure Monitor monitor Azure Virtual Desktop by using Azure Advisor customize Azure Monitor workbooks for Azure Virtual Desktop monitoring optimize session host capacity and performance manage active sessions and application groups monitor and optimize autoscaling results | ||||||||||
| Configuring and Operating Windows Virtual Desktop on Microsoft Azure Microsoft Configuring course outline | ||||||||||
Other Microsoft examsMOFF-EN Microsoft Operations Framework Foundation62-193 Technology Literacy for Educators AZ-400 Microsoft Azure DevOps Solutions DP-100 Designing and Implementing a Data Science Solution on Azure MD-100 Windows 10 MD-101 Managing Modern Desktops MS-100 Microsoft 365 Identity and Services MS-101 Microsoft 365 Mobility and Security MB-210 Microsoft Dynamics 365 for Sales MB-230 Microsoft Dynamics 365 for Customer Service MB-240 Microsoft Dynamics 365 for Field Service MB-310 Microsoft Dynamics 365 for Finance and Operations, Financials (2023) MB-320 Microsoft Dynamics 365 for Finance and Operations, Manufacturing MS-900 Microsoft Dynamics 365 Fundamentals MB-220 Microsoft Dynamics 365 for Marketing MB-300 Microsoft Dynamics 365 - Core Finance and Operations MB-330 Microsoft Dynamics 365 for Finance and Operations, Supply Chain Management AZ-500 Microsoft Azure Security Technologies 2023 MS-500 Microsoft 365 Security Administration AZ-204 Developing Solutions for Microsoft Azure MS-700 Managing Microsoft Teams AZ-120 Planning and Administering Microsoft Azure for SAP Workloads AZ-220 Microsoft Azure IoT Developer MB-700 Microsoft Dynamics 365: Finance and Operations Apps Solution Architect AZ-104 Microsoft Azure Administrator 2023 AZ-303 Microsoft Azure Architect Technologies AZ-304 Microsoft Azure Architect Design DA-100 Analyzing Data with Microsoft Power BI DP-300 Administering Relational Databases on Microsoft Azure DP-900 Microsoft Azure Data Fundamentals MS-203 Microsoft 365 Messaging MS-600 Building Applications and Solutions with Microsoft 365 Core Services PL-100 Microsoft Power Platform App Maker PL-200 Microsoft Power Platform Functional Consultant PL-400 Microsoft Power Platform Developer AI-900 Microsoft Azure AI Fundamentals MB-500 Microsoft Dynamics 365: Finance and Operations Apps Developer SC-400 Microsoft Information Protection Administrator MB-920 Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP) MB-800 Microsoft Dynamics 365 Business Central Functional Consultant PL-600 Microsoft Power Platform Solution Architect AZ-600 Configuring and Operating a Hybrid Cloud with Microsoft Azure Stack Hub SC-300 Microsoft Identity and Access Administrator SC-200 Microsoft Security Operations Analyst DP-203 Data Engineering on Microsoft Azure MB-910 Microsoft Dynamics 365 Fundamentals (CRM) AI-102 Designing and Implementing a Microsoft Azure AI Solution AZ-140 Configuring and Operating Windows Virtual Desktop on Microsoft Azure MB-340 Microsoft Dynamics 365 Commerce Functional Consultant MS-740 Troubleshooting Microsoft Teams SC-900 Microsoft Security, Compliance, and Identity Fundamentals AZ-800 Administering Windows Server Hybrid Core Infrastructure AZ-801 Configuring Windows Server Hybrid Advanced Services AZ-700 Designing and Implementing Microsoft Azure Networking Solutions AZ-305 Designing Microsoft Azure Infrastructure Solutions AZ-900 Microsoft Azure Fundamentals PL-300 Microsoft Power BI Data Analyst PL-900 Microsoft Power Platform Fundamentals MS-720 Microsoft Teams Voice Engineer DP-500 Designing and Implementing Enterprise-Scale Analytics Solutions Using Microsoft Azure and Microsoft Power BI PL-500 Microsoft Power Automate RPA Developer SC-100 Microsoft Cybersecurity Architect MO-201 Microsoft Excel Expert (Excel and Excel 2019) MO-100 Microsoft Word (Word and Word 2019) MS-220 Troubleshooting Microsoft Exchange Online DP-420 Designing and Implementing Cloud-Native Applications Using Microsoft Azure Cosmos DB MB-335 Microsoft Dynamics 365 Supply Chain Management Functional Consultant Expert MB-260 Microsoft Dynamics 365 Customer Insights (Data) Specialist AZ-720 Troubleshooting Microsoft Azure Connectivity 700-821 Cisco IoT Essentials for System Engineers (IOTSE) MS-721 Microsoft 365 Certified: Collaboration Communications Systems Engineer Associate MD-102 Microsoft 365 Certified: Endpoint Administrator Associate MS-102 Microsoft 365 Administrator | ||||||||||
| killexams.com deliver most exact and updated AZ-140 dumps with genuine exam Questions and Answers for new syllabus of AZ-140 AZ-140 Exam. Practice our AZ-140 real questions and Answers to Improve your knowledge and pass your exam with High Marks. We guarantee your success in the Test Center, covering every one of the points of exam and construct your Knowledge of the AZ-140 exam. Pass beyond any doubt with our genuine questions. | ||||||||||
| AZ-140 Dumps AZ-140 Braindumps AZ-140 Real Questions AZ-140 Practice Test AZ-140 dumps free Microsoft AZ-140 Configuring and Operating Windows Virtual Desktop on Microsoft Azure http://killexams.com/pass4sure/exam-detail/AZ-140 Question: 49 HOTSPOT Which users can create Pool4, and which users can join session hosts to the domain? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Answer: Question: 50 DRAG DROP You need to evaluate the RDS deployment in the Seattle office. The solution must meet the technical requirements. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Answer: Question: 51 HOTSPOT Your company has the offices shown in the following table. The company has an Azure Active Directory (Azure AD) tenant named contoso.com that contains a user named User1. Users connect to a Windows Virtual Desktop deployment named WVD1. WVD1 contains session hosts that have public IP addresses from the 52.166.253.0/24 subnet. Contoso.com has a conditional access policy that has the following settings: � Name: Policy1 � Assignments: � Users and groups: User1 � Cloud apps or actions: Windows Virtual Desktop � Access controls: � Grant: Grant access, Require multi-factor authentication � Enable policy: On For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Answer: Question: 52 You need to ensure the resiliency of the user profiles for the Boston office users. The solution must meet the user performance requirements. What should you do? A. Modify the Account kind setting of storage1. B. Modify the replication settings of storage1. C. Implement Azure Site Recovery. D. Configure Cloud Cache. Answer: D Explanation: Reference: https://docs.microsoft.com/en-us/azure/architecture/example-scenario/wvd/windows-virtual-desktop-fslogix Question: 53 Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Windows Virtual Desktop host pool that contains five session hosts. The session hosts run Windows 10 Enterprise multi-session. You need to prevent users from accessing the internet from Windows Virtual Desktop sessions. The session hosts must be allowed to access all the required Microsoft services. Solution: You modify the IP configuration of each session host. Does that meet the goal? A. Yes B. No Answer: B Question: 54 DRAG DROP You have an Azure subscription that contains the storage accounts shown in the following table. You have a custom generalized Windows 10 image. You plan to deploy an Azure Virtual Desktop host pool that will use the custom image and FSLogix profile containers. You need to recommend which storage accounts to use for the custom image and the profile containers. The solution must meet the following requirements: Minimize costs to store the image. Maximize performance of the profile containers. Which account should you recommend for each type of content? To answer, drag the appropriate accounts to the correct content type. Each account may be used once, more than once, or not at all. You many need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Answer: Explanation: A picture containing text Description automatically generated Question: 55 You have an Azure storage account that contains the generalized Windows 10 disk images shown in the following table. You need to create an image that will be used to deploy an Azure Virtual Desktop session host. Which disk should you use? A. Disk1 B. Disk2 C. Disk3 D. Disk4 Answer: A Explanation: Reference: https://docs.microsoft.com/en-us/azure/virtual-desktop/set-up-customize-master-image Question: 56 You have an Azure Virtual Desktop deployment. You need to monitor the deployment by using the Azure Virtual Desktop Insights solution in Azure Monitor. What should you use as the Diagnostic settings destination for the host pool? A. Event hub B. Log Analytics workspace C. Storage account Answer: B Question: 57 DRAG DROP You have an Azure Virtual Desktop deployment. You plan to create the host pools shown in the following table. You need to recommend the virtual machine size for each host pool to meet the session host requirements. Answer: Explanation: Table Description automatically generated Question: 58 You have an Azure Virtual Desktop deployment that contains the resources shown in the following table. You need to enable just-in-time (JIT) VM access for all the session hosts. What should you do first? A. Deploy Azure Bastion to VNET1. B. Assign network security groups (NSGs) to the network interfaces of the five session hosts. C. Configure Access control (IAM) for HostPool1. D. Assign a network security group (NSG) to Subnet1. Answer: B Question: 59 You have an Azure Virtual Desktop personal host pool named Pool1 that contains 20 Azure AD-joined session hosts. You need to ensure that only approved virtual machine extensions are installed on the Pool 1 session hosts. The solution must minimize administrative effort. What should you use? A. Azure Resource Manager (ARM) templates B. Azure Policy C. Windows Admin Center D. Group Policy Answer: B Question: 60 You need to modify the custom virtual machine images to meet the deployment requirements. What should you install? A. the RSAT: Remote Desktop Services Tools optional feature B. the Azure Virtual Desktop Agent C. the Microsoft Monitoring Agent D. the FSLogix agent Answer: D Explanation: Reference: https://docs.microsoft.com/en-us/azure/virtual-desktop/set-up-customize-master-image For More exams visit https://killexams.com/vendors-exam-list Kill your exam at First Attempt....Guaranteed! | ||||||||||
|
LESSON 5: COMPENSATION AND BENEFITSUnderstand all the things that must be considered when designing a compensation and benefits package.LESSON 6: EMPLOYEE HEALTH AND SAFETYLearn the ins and outs of complying with OSHA, protecting against workplace hazards, and investigating, recording, and preventing accidents and employee illnesses.LESSON 7: THE LEGAL ENVIRONMENTGain knowledge of employment law as well as an understanding of equal employment opportunity, avoiding discrimination, and what happens when an employee files an EEOC claim.LESSON 8: MAKING HR DECISIONSLearn how to make decisions based on various company growth strategies and how to use HRIS Software as well as job analysis as a tool for decision-making.LESSON 9: AFFIRMATIVE ACTIONLearn the full spectrum of affirmative action, how to create an affirmative action plan, and information on the AAP you will need to know.LESSON 10: DIVERSITYUnderstand what diversity is and why it is a good thing in an organization as you learn to manage it and handle conflict.LESSON 11: EMPLOYEE RIGHTS AND DISCIPLINELearn the laws that protect employee rights and privacy and how to properly monitor and document behavior and discipline employees.LESSON 12: TERMINATIONUnderstand the alternatives to firing as well as how to prepare for termination including proper separation agreements as well as what to do in the event of wrongful discharge.LESSON 13: INVESTIGATIONSLearn why it is so important to investigate problems as well as the steps of an effective investigation including preparing, conducting, and wrapping it up.LESSON 14: MANAGING LABOR RELATIONSGet a quick overview of the history of unions as you learn how they work and why employees join them.LESSON 15: CREATING A HIGH-PERFORMANCE WORKPLACELearn how to ask employees for input and act on it, delegate authority, keep communication open, and continuously ask for feedback as you strive to develop a high-performance workplace.LESSON 16: GLOBAL HUMAN RESOURCESUnderstand the basics of staffing strategy, cultural differences, HR in other countries, choosing global employees, and issues faced by expatriates.LESSON 17: RETENTIONLearn the top reasons employees leave a company and how you can encourage them to stay as well as the importance of succession planning.LESSON 18: MOTIVATION, REWARDS, AND RECOGNITIONFind out fun ways to motivate workers and gain nine strategies for creating a great rewards program.LESSON 19: PREPARING FOR THE PHR EXAMGain information on externships and internships as you review the basics of the PHR exam and begin to study.Formerly known as Microsoft Operations Manager v3, System Center Operations Manager 2007 provides end-to-end event, service and application monitoring and reporting. The platform supports Service Model Language (SML) for monitoring IT and software services -- required for service-level agreements -- and features audit collection services for compliance auditing and a customizable reporting tool. At the Microsoft Management Summit, which started Tuesday in San Diego, the Redmond, Wash., software giant also announced a technology licensing agreement with EMC that will bolster the network management capabilities of System Center Operations Manager 2007. As part of the deal, Microsoft said it will integrate EMC's Smarts network discovery and health monitoring software into a future version of Operations Manager. In addition, Microsoft, EMC and Cisco unveiled a pact to develop a set of network common models that exploit the SML to simplify network management. As part of the arrangement, the companies have submitted SML -- which is based on Microsoft's System Definition (SDM) Model -- for adoption as a standard to the W3C. That would allow partners and customers to manage software and hardware, as well as Windows systems, on the System Center platform. Operations Manager 2007 is just one of several System Center products Microsoft is preparing for release this year. System Center Configuration Manager 2007, formerly referred to as Systems Management Server v4, is scheduled to ship this summer. To add more value to the software configuration and deployment platform, Microsoft plans to roll out an add-on for Configuration Manager 2007 after it ships that will support Intel's next-generation vPro client management technology, code-named Weybridge, which is also due for a midyear release. Microsoft also highlighted its progress in virtualization, backup and service management. System Center Virtual Manager, formerly code-named Carmine, will move into Beta 2 testing in the next 45 days, the company said. And the second version of System Center Data Protection Manager -- which will provide backup and recovery for SharePoint 2007, Virtual Server 2005, Windows XP and Windows Vista -- will move into Beta 2 testing in the next 30 days. Microsoft also announced System Center Service Manager, the formal name of its former Service Desk offering, and said plans to release the first beta in the next 30 days. In addition, Microsoft announced an update for partners and customers awaiting Systems Management Server Service Pack 3. SMS Service Pack 3 with AssetMetrix software asset-management capabilities will be released to manufacturing this spring, the company said.
Central to the SNA network is the SNA server, which is responsible for performing connections between local and remote hosts on a local area network (LAN). Note: An unqualified reference to Windows means all Windows platforms - Windows NT, Windows 95, Windows 98, and Windows 32s.
The following figure shows an SNA network. Typical SNA Network Configuration
It is assumed that you already have completed installation of the SNA server product. Before you can configure the SNA server, verify that the following tasks have been completed.
After you have installed the SNA server and link supports, use the SNA Server Administration Program (SNA Server Admin) to perform the following tasks:
Configuring the ServerConfigure the SNA server by specifying the local Network Name and Control Point Name. Specifying the Connection NameSpecify the connection name (for example, 802.2 Token Ring, SDLC, or X.25) and other properties that are appropriate to your configuration. Connection properties are the software components of the SNA server that communicate through the device driver to a particular communications adapter. Configuring Logical UnitsPerform the following steps to configure the desired number of logical units:
Defining LU-LU Pairs and Communications Mode PropertiesDefine the local LU-remote LU pairs, and specify the properties of the communications mode to be used between each pair. If site-naming conventions permit, specify the mode name SASAPPC. The APPC access method uses this mode name if the APPC_LU62MODE variable has not been defined. See SAS/CONNECT and SAS/SHARE Options for information about setting APPC_LU62MODE. Specify the minimum contention-winner parameter, which is relevant for SAS software because only contention-winner sessions are used for locally initiated communication. Communication between SAS/CONNECT local and remote hosts requires only one contention-winner session. However, this limit affects the number of data sets that can be accessed concurrently by means of the SAS/CONNECT Remote Library Services or a SAS/SHARE server. When defining session limits, define enough sessions so that session limits will never be reached. If session limits are reached, the next time a user attempts to connect to a remote host with SAS/CONNECT or a client host attempts to access a SAS/SHARE server, the APPC layer will not return to the application layer until a session is available. Although a lengthy wait may seem like an error condition (such as no response from SAS or a loop), the underlying APPC layer is waiting for a session to become available. You have completed the configuration of a Windows NT SNA server.
Client configuration tasks are based on the platform on which the client is running:
Tasks for configuring a Windows NT, a Windows 95, and a Windows 98 client are identical. Configuring a Windows NT, a Windows 95, or a Windows 98 Host as a Local Host or a SAS/SHARE ClientUse the SNA Server Client Setup Program to configure Windows NT, Windows 95, and Windows 98 clients. This section highlights the general tasks that you perform to configure an SNA client. For complete details, see the Microsoft SNA Server Installation Guide and the Microsoft SNA Server Administration Guide. (Contact the Microsoft Corporation for information about this documentation.) Perform the following tasks:
If you intend to use the Windows NT, Windows 95, or Windows 98 computer strictly as a local host connecting to a remote host in a SAS/CONNECT session or as a client accessing a SAS/SHARE server, you have successfully completed the configuration process. Configuring a Windows NT, a Windows 95, or a Windows 98 Host as a Remote Host or as a SAS/SHARE ServerIf you intend to use either of these computers as a remote host for a SAS/CONNECT session or as a SAS/SHARE server, you must perform additional configuration tasks.
SASTP62 Transaction ProgramFor Version 7 and later, the APPC access method performs dynamic TP naming which automatically generates the SASTP62 TP definition for you. Note: Dynamic TP naming is only available when communicating between two Version 7 (or later) sessions. For Version 6.12 and earlier, you must still define a SASTP62 transaction program at the host where a SAS/SHARE server will be executing or where a remote SAS/CONNECT session will be established. To define the SASTP62 transaction program in the registry, specify the following command: TPSETUP -TP SASTP62 SASRMT Transaction ProgramYou must define a SASRMT transaction program at the host where a remote SAS/CONNECT session will be established. To define the SASRMT transaction program in the registry, specify the following command: TPSETUP -TP SASRMT Note: For Windows NT, you must run the SASRMT transaction program as an application, not as an NT service. Therefore, make sure that you start the Microsoft program TPSTART.EXE before allowing users to establish SAS/CONNECT sessions with remote hosts. You have completed the configuration of the Windows NT, Windows 95, or Windows 98 host as a SAS/CONNECT remote host or a SAS/SHARE server. Configuring a Windows 32s ClientUse the SNA Server Client Setup Program to configure a Windows 32s client. This section highlights the general tasks that you perform to configure an SNA client. For complete details, see the Microsoft SNA Server Installation Guide and the Microsoft SNA Server Administration Guide. Note: A Windows 32s host is supported only as a local host that connects to a remote host in a SAS/CONNECT session. Perform the following tasks:
You have completed the configuration of the Windows 32s client. For details about how to install and configure the SNA server and SNA clients using the SNA Server Setup Program, see the Microsoft SNA Server Installation Guide and the Microsoft SNA Server Administration Guide. For details about configuring Windows NT Host Security Integration features, see Microsoft SNA Server Getting Started and Installing and Configuring Host Security Integration. Contact the Microsoft Corporation to obtain information about this documentation. Copyright 1999 by SAS Institute Inc., Cary, NC, USA. All rights reserved. Learning how to change and configure Microsoft Edge Proxy Settings is quite important to users who would like to protect their online privacy. Many web browsers, including Microsoft Edge, have features that support proxy. However, some users don’t know to go about it, which is relatively simple. A proxy server intercepts your computer network traffic before it gets to you; it’s just another remote computer. The are many reasons why users switch to a proxy, but the main one is to get an extra measure of online security.
What is Edge Proxy Server?The Edge proxy server is a server that is located on the intranet and connects to the main server via the Internet. It is not bound to other proxy servers. It resolves a request for content from a local cache and proxying from the original server. Edge proxy server cannot request to any other proxy server. The proxy works so that your IP address will not be revealed. You access the Internet using the proxy’s IP address. It is a great way to ensure you are safe online, especially for sites or malicious people tracking your activities online. It’s good to know that there are paid and free proxy server services. There are two ways to configure a proxy server in MS Edge and it’s simple. You can use the manual way or simply use the automatic configuration. We will discuss this later in this article. This post will elaborate on changing and configuring Microsoft Edge Proxy settings. If you want to access geo-restricted content, protect your devices or conceal your IP address, you are in the right place. Continue reading. Changing and configuring Edge proxy settings is a straightforward process, but you don’t need some specific browser proxy settings to surf on standard web pages. However, these settings can be changed to access geo-restricted pages or just for security purposes. To change and configure Microsoft Edge proxy settings, use any of the following methods:
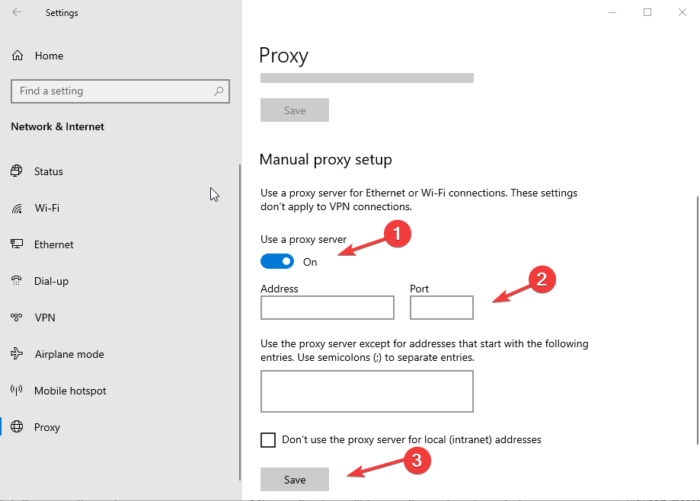
To turn off proxy settings in Microsoft Edge, go to the menu (three dots) on the top right and scroll down to Settings. Choose System and, on the left side, click on Open your computer’s proxy settings. From there, toggle off the buttons next to Automatically detect settings, Use setup script, and Use a proxy server. To complete the process click Save. 1] Manual proxy setup
To set up a proxy setting manually, you need to use Wi-Fi or Ethernet internet connections. If you are connected to any VPN, you need to disable it while setting up and using the proxy server. Here is how:
Read: Can’t connect to the proxy server says Microsoft Edge 2] Automatic proxy setup
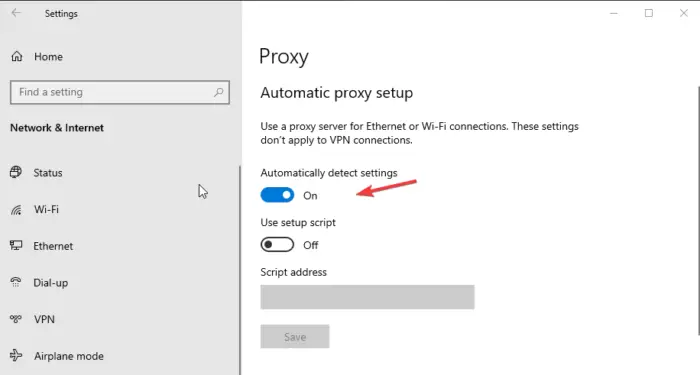
If you feel setting up a proxy server manually is a lot of work, you can choose the automatic mode option. As in the manual setup, you need only to use Ethernet or Wi-Fi connections. Deactivate any VPN running on your computer. This setup automatically detects settings and uses a setup script. Here is how:
Let us know if these methods helped you change and configure Microsoft Edge proxy settings. Read: Ethernet works but not WiFi in Windows. 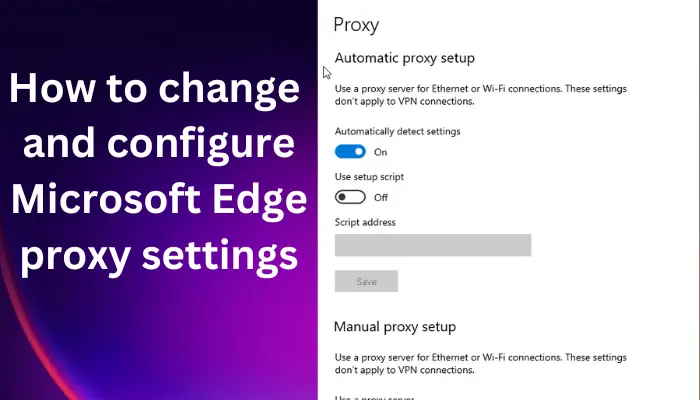
Windows 11 natively supports passkeys, a modern passwordless technology that lets you sign in to your online accounts using Windows Hello. From a security standpoint, passkeys are as effective as using an authenticator app. But they’re even easier to use, and that rare combination of secure and convenient has already catapulted passkeys to a level of acceptance and usage those other two solutions never achieved. Note: Be sure to configure your Microsoft account securely with two-step authentication and multiple alternate sign-in and security verification methods using the instructions I outline in a previous post. This write-up, like that one, is based on content I’ve created for new chapters of all-new content in the Windows 11 Field Guide, in this case one that covers passkeys and security keys. 2023 was notable for so many reasons, but one of the biggest shifts was the rapid spread of passkey support across popular online accounts from Amazon, Apple, Google, and many others. But despite doing more than any of these other companies to enable a passwordless world, Microsoft was curiously quiet when it came to passkeys this past year. Meanwhile, Google was widely acclaimed for making passkeys the default sign-in option for its online accounts this past October. This, despite the fact that Microsoft had allowed its customers to literally remove the password from their Microsoft accounts for over two years by that point. Windows Intelligence In Your InboxSign up for our new free newsletter to get three time-saving tips each Friday — and get free copies of Paul Thurrott's Windows 11 and Windows 10 Field Guides (normally $9.99) as a special welcome gift! "*" indicates required fields But this is on Microsoft: Aside from briefly mentioning passkey management as one of the many new features in Windows 11 version 23H2, the software giant didn’t promote its support for this technology in any meaningful way this past year. Nor does Windows 11 really mention passkeys in any meaningful way when you access your Microsoft account, while Google, especially, makes a big deal about it when you access its accounts on the web. Instead, Microsoft seems content to let its users keep using the passwordless sign-in functionality provided most commonly by authenticator mobile apps. But that’s not the full story. As I wrote in The Secret Lives of Passkeys (Premium), Microsoft silently saves a passkey to your PC’s Trusted Platform Module (TPM) security chip when you sign in to Windows 11 with a Microsoft account or Microsoft work or school account. And so the passkey for one of your most important online accounts is already there on the PC, and you can authorize its use online, in any web browser, using Windows Hello (PIN or biometric, whichever you have configured), the secure method you’re already using to sign in to your Microsoft account (or work or school account) when you fire up the PC. So that’s a lackluster tip, I guess: To create a passkey for your Microsoft account, just do nothing. It’s already there. Of course, you still have to know how to use that passkey. And you may have other Microsoft accounts, and would like to create a passkey for those accounts on this PC too. And you use a phone: Can you create a passkey for your Microsoft account there? Should you? And if so, how? First, a quick explainer. What are passkeys?At a high level, a passkey is another alternative for bypassing the password associated with an online account, albeit one that is based on an industry standard with broad adoption from platform makers and service providers. Like authenticator apps, passkeys help protect against and phishing attacks and other password-related compromises. And as with authenticator apps, passkeys rely on the modern security technologies we take for granted these days on our devices, including secure, encrypted storage of some kind and secure sign-in technologies like PINs and, ideally, biometrics like facial and fingerprint recognition. There is one wrinkle: Each passkey you create is specific to the device on which it was created. That means you will have a different passkey for each supported online account on one PC. And a different passkey for each supported account on each of your PCs and other devices. This may seem complex, but in practice, it works seamlessly after a one-time set up process. And unlike with an authenticator app or security key, you don’t have to have or use another device when you need to sign-in. Once you’ve stored a passkey on your PC (or Microsoft has done so for you with your Microsoft account), subsequent sign ins, on the web or in apps will be seamless. When you’re prompted by some online service to sign in for whatever reason, all you’re expected to know is the email address associated with the account. (And in most cases, that will be auto-filled by your browser, OS, or password manager anyway.) Then, instead of typing a password or dealing with an authenticator app on your phone, you can authenticate yourself using a secure Windows Hello PIN or biometric method. When you prove who you are to Windows, the system will communicate this success back to the service that prompted you to sign-in. And because it trusts that this authentication is both correct and secure—you configured it together, after all—it grants you access to the service. Passkeys can also be implemented in Windows (and elsewhere) using security keys, as noted, or in certain password managers. What we’re discussing here is the native platform capability in Windows. What Windows 11 version 23H2 adds is passkey management capabilities (noted below). But there’s more work to do: The Microsoft account’s support for passkeys is not particularly obvious, and Windows 11 doesn’t (yet?) sync your passkeys through your Microsoft account, a capability that would make passkey usage (for all of your accounts) much more seamless. Today, you need to manually create a passkey for each account on each PC. We’ll get there, I bet. But for now, I’ll keep this focused specifically on creating and using a passkey with your Microsoft account on a Windows 11-based PC. (This works nearly identically for Microsoft work or school accounts as well.) Note: Windows has long supported authenticating online accounts using physical security keys like those made by Yubico, and these hardware fobs also support passkeys. Security keys have their place, but their complexity and cost make them non-starters for most individuals. Authenticator apps and passkeys are much more convenient. But no worries, I’m covering security keys in the book too. Create a passkey for a Microsoft accountIf you sign in to Windows 11 with a Microsoft account, you’re done: Microsoft already created a passkey for that account, and you can see it in the Settings app by navigating to Accounts > Passkeys. On this PC, there is just a single passkey, for the Microsoft account used to sign in to Windows 11.
If this is all you need, you can move on to the next section. But if you have other Microsoft accounts, you can create a passkey for each on this PC too. And you create a passkey for a Microsoft account the same way you create any other additional account sign-in or verification method, by navigating to the Additional security options page on the Microsoft account website, authenticating as prompted, and then clicking “Add a new way to sign in or verify.” (Note that this may be easier to do in a secondary web browser as handling multiple Microsoft accounts in a single browser can be problematic.)
In the “Select an additional way to verify or sign in” dialog that appears, click “Use your Windows PC.” The “Use Windows Hello to sign in to your account” page appears. Click “Next.” Windows 11 will display a prompt explaining that the sign-in data for your Microsoft account will be stored on this PC, allowing you to sign-in to that account later using this credential. Click “OK.” Windows will then prompt you to authenticate using Windows Hello PIN, facial recognition, or fingerprint recognition so that it can securely save the passkey on this PC. (This will vary according to which methods you’ve configured. Click “More choices” here to choose a different method than the one presented.)
Once you’ve authenticated using Windows Hello, Windows will store the account credential in the TPM’s secure storage on the PC. And the Microsoft account website will note that you can now use Windows Hello to sign-in to this account in the future, instead of your password (or a phone-based verification method or whatever other methods you’ve configured). Sign-in to your Microsoft account on a PC using a passkeyTo use the passkey to sign-in to your Microsoft account, click “Other ways to sign in” when prompted in the future. (Note that you will not see this option at the Windows 11 lock screen: Windows already provides Windows Hello device-specific sign-in capabilities and these methods are as seamless as they can be. I used an InPrivate browser window for these shots.)
This prompt will typically default to whatever authentication method you used most recently. But you can choose between different ways to authenticate yourself. Click “Sign in with Windows Hello or a security key” and then authenticate using whichever method you prefer that is available on that PC. (Windows Hello in this case.)
And that’s it: You’ve signed into your account securely and seamlessly, and without needing to fish your phone out of your pockets and deal with its on-screen prompts. Manage passkeys in Windows 11 version 23H2Passkey management is an interesting course in part because many online accounts provide limited capabilities in this regard. But your Microsoft account is among the worst: Once you create a passkey on a particular PC from the Microsoft account website, there’s no way to manage that from the web: It does not appear in the list of additional sign-in and verification methods alongside your password, email addresses, authenticator app, and other methods. Other companies, including Google, offer centralized passkey management on their online account management websites. But it doesn’t matter. If your PC is lost or stolen, your passkey stays safe because it’s stored in encrypted storage and further protected via a PIN or biometric authentication method. But I still expect this to change in the future, if only because customers will expect to be able to remotely delete passkeys or in some way disconnect existing passkeys from the underlying service. Until that happens, you can manage the passkeys on a PC using the Settings app in Windows 11 version 23H2 and newer, as noted above: Navigate to Accounts > Passkeys settings to see what’s available. As expected, the capabilities are limited to deleting passkeys one at a time: Just click the “See more” (“…”) item next to a passkey and then “Delete passkey.” Note that these passkeys are system-wide: I created some of those using a different Windows 11 sign-in account. As long as I have admin privileges, I can delete any and all passkeys stored on that PC, except for the passkey associated with the account I’m currently using.
And that’s literally all you can do with this new Windows 11 version 23H2 feature. What about mobile?Because Microsoft doesn’t have its own mobile platform anymore, those with a Microsoft account (or Work or School account) tend to approach their Android phones and tablets, iPhone, and iPads from the perspective of the apps they use there. That is, we sign in to this account when we need to configure our Microsoft account in a Microsoft (Outlook, Microsoft 365, OneDrive, etc.) or third-party (Gmail, Google Calendar, etc.) app, using some form of password auto-fill (native or third-party), and then hopefully configure an authenticator app like Microsoft Authenticator to further protect our Microsoft account and other online accounts. And that does appear to be Microsoft’s solution on mobile, as it does not support saving passkeys for Microsoft accounts (or Microsoft work or school accounts) on mobile. Instead, you’re expected to use Microsoft Authenticator, the idea being that it works similarly to a passkey since you can verify sign-in attempts using that app on the same device on which you’re making the sign-in attempt. That is, while an app on a phone is a bit inconvenient when you’re using a PC, it’s not at all inconvenient when you’re using that phone. So the benefit of a passkey would be minimal on that one device. This is perhaps misguided. Like Windows 11, these mobile platforms—Android, iOS, and iPadOS—all support passkeys natively, each device type has secure storage in a TPM-like security chip, and each supports secure PIN and biometric sign-in methods to protect those passkeys. And you won’t typically use Authenticator on an Android tablet or iPad. Using a passkey on those devices would be convenient too. Maybe someday. Microsoft Outlines New Outlook for Windows Rollout PlanMicrosoft will deliver organizations advance notice of the coming change. Microsoft is planning to replace the current Outlook for Windows client application with a new product, but it could take maybe two years for that transition to get finalized for organizations. That view was outlined by Microsoft luminaries Margie Clinton, group product manager on the Outlook team, and Robert Novitskey, partner engineering manager for Outlook for Windows, in an online presentation. The presentation was published last week, but it's noted in this Sept. 12 Microsoft announcement. The two Microsoft luminaries mostly described why Microsoft is redoing its 25-year-old Outlook for Windows product. Some planned feature improvements were highlighted. They also addressed IT department concerns about the transition's timing. Clinton said that Microsoft had no strict timeline for the end of life of the classic Outlook for Windows product. Microsoft's timing is "going to be determined on overall readiness, based on us delivering the core capabilities to the point where we believe that we're ready for opt out." However, she added that the end of the classic product is coming, and it would occur maybe "in a little bit more than two years." The online presentation offered the following slide, showing the expected phases for rolling out the new Outlook for Windows client app: 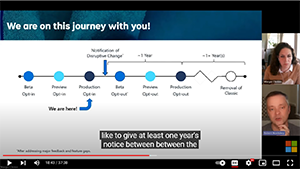
Novitskey noted that Microsoft tries to deliver a one-year advance notice of disruptive changes for its commercial software. IT pros will get such a notice via the Message Center. Microsoft eventually will switch the apps, though, which Novitskey called a "cutover":
Some things won't work in the new Outlook for Windows, namely COM add-ins. Instead, the new Outlook for Windows will use Web add-ins. The following slide made those declarations: 
Microsoft initially plans to roll out the new Outlook for Windows app as an option for users, with a toggle switch to try it located at the top right corner of the legacy client. The toggle switch, currently in the "Off" position by default, now appears for organizations that are using the monthly enterprise channel releases of Microsoft 365, Novitskey said. IT pros initially will get Registry and Group Policy Object controls over whether end users can see this toggle switch, before total replacement with the new app. The IT controls were briefly outlined in the following slide: 
Novitskey noted that the coming new Outlook for Windows client app can be a big change for large organizations with lots of users. He suggested that Microsoft's "support can work with you to kind of develop a personalized timeline, and they can secure kind of whatever extensions you may need for your tenant." The new Outlook for Windows has a more simplified user interface, which looks somewhat like its Outlook on the Web predecessor. However, Microsoft is really making the switch to the new app because its current Outlook for Windows app is available in more than three offerings that all work differently, Clinton explained. Instead, with the new product, Microsoft wants to "apply all of our engineering energy on Windows into delivering and then maintaining a single, fast and agile codebase," she added. This change will allow Microsoft to address customer issues in hours and days, rather than weeks and months. The new Outlook for Windows client will be customizable for various users. It also will get Microsoft's artificial intelligence enhancements, which Microsoft believes will deliver a "10x productivity" improvement, Clinton said. Microsoft really wants to earn "Outlook love" with the new client, and so is actively seeking early feedback from organizations, Clinton indicated. About the Author Kurt Mackie is senior news producer for 1105 Media's Converge360 group. Copyright 2024 BBC. All rights reserved. The BBC is not responsible for the content of external sites. Read about our approach to external linking. Beta Terms By using the Beta Site, you agree that such use is at your own risk and you know that the Beta Site may include known or unknown bugs or errors, that we have no obligation to make this Beta Site available with or without charge for any period of time, nor to make it available at all, and that nothing in these Beta Terms or your use of the Beta Site creates any employment relationship between you and us. The Beta Site is provided on an “as is” and “as available” basis and we make no warranty to you of any kind, express or implied. In case of conflict between these Beta Terms and the BBC Terms of Use these Beta Terms shall prevail. | ||||||||||
AZ-140 tricks | AZ-140 tricks | AZ-140 testing | AZ-140 approach | AZ-140 syllabus | AZ-140 study | AZ-140 basics | AZ-140 techniques | AZ-140 study help | AZ-140 course outline | | ||||||||||
Killexams exam Simulator Killexams Questions and Answers Killexams Exams List Search Exams |








![[cautionend]](https://www.sfu.ca/sasdoc/sashtml/common/images/cautend.gif)
![[IMAGE]](https://www.sfu.ca/sasdoc/sashtml/comm/images/01313947.gif)