Certified Internal Auditor - Part 3- Business Analysis and Information Technology Exam Braindumps
Killexams.com IIA-CIA-Part3 Exam Braindumps contain complete question pool, updated in April 2024 including VCE exam simulator that will help you get high marks in the exam. All these IIA-CIA-Part3 exam questions are verified by killexams certified professionals and backed by 100% money back guarantee.
IIA-CIA-Part3 techniques - Certified Internal Auditor - Part 3, Business Analysis and Information Technology Updated: 2024 | ||||||||
| IIA-CIA-Part3 Dumps and practice questions with Real Questions, that?s all you need | ||||||||
 |
||||||||
|
||||||||
|
Exam Code: IIA-CIA-Part3 Certified Internal Auditor - Part 3, Business Analysis and Information Technology techniques January 2024 by Killexams.com team | ||||||||
IIA-CIA-Part3 Certified Internal Auditor - Part 3, Business Analysis and Information Technology Test Detail: The IIA IIA-CIA-Part3 exam, also known as Certified Internal Auditor - Part 3, Business Analysis and Information Technology, is designed to assess the knowledge and skills of professionals in the areas of business analysis and information technology. This exam focuses on evaluating the candidate's understanding of business processes, risks, and controls, as well as their ability to apply information technology concepts in an auditing context. The following description provides an overview of the IIA IIA-CIA-Part3 exam. Number of Questions and Time: The IIA IIA-CIA-Part3 exam typically consists of approximately 100 multiple-choice questions. The exact number of questions may vary. Candidates are given 2.5 hours (150 minutes) to complete the exam. The passing score is typically 600 or higher, on a scaled score range of 250 to 750. Course Outline: To prepare for the IIA IIA-CIA-Part3 exam, candidates can enroll in training programs that cover the key Topics and competencies required for business analysis and information technology in the context of internal auditing. These courses provide a comprehensive understanding of business processes, risks, controls, and the role of information technology. The course outline may include the following topics: 1. Business Processes and Risks: - Understanding business processes and their components - Identifying and assessing risks in business processes - Applying risk management techniques - Internal control frameworks and their role in managing risks 2. Business Process Analysis and Improvement: - Techniques for analyzing business processes - Identifying process inefficiencies and improvement opportunities - Implementing process improvement initiatives - Monitoring and measuring process performance 3. Information Technology and Internal Audit: - Understanding the role of information technology in organizations - IT governance frameworks and principles - Assessing IT risks and controls - Auditing IT systems and applications 4. Information Technology Tools and Techniques: - IT general controls and application controls - Data analytics and data mining techniques - Cybersecurity and information security controls - Emerging technologies and their impact on internal auditing Exam Objectives: The IIA IIA-CIA-Part3 exam aims to evaluate the candidate's knowledge and skills in business analysis and information technology within the context of internal auditing. The exam objectives include the following: 1. Understanding business processes and their associated risks. 2. Applying risk management techniques and internal control frameworks. 3. Analyzing and improving business processes to enhance efficiency and effectiveness. 4. Assessing IT risks and controls and their impact on business processes. 5. Utilizing IT tools and techniques in the internal audit process. 6. Understanding emerging technologies and their implications for internal auditing. Exam Syllabus: The IIA IIA-CIA-Part3 exam syllabus covers the key Topics and competencies required to excel in business analysis and information technology in the context of internal auditing. The syllabus includes the following areas of study: - Business processes and their risks - Internal control frameworks and risk management - Business process analysis and improvement techniques - IT governance, risks, and controls - Information technology tools and techniques in auditing - Emerging technologies and their impact on internal auditing | ||||||||
| Certified Internal Auditor - Part 3, Business Analysis and Information Technology IIA Information techniques | ||||||||
Other IIA examsCCSA Certification in Control Self-Assessment (IIA-CCSA)CFSA Certified Financial Services Auditor (IIA-CFSA) IIA-CIA-Part1 Certified Internal Auditor - Part 1, The Internal Audit Activitys Role in Governance, Risk, and Control IIA-CIA-Part2 Certified Internal Auditor - Part 2, Conducting the Internal Audit Engagement IIA-CIA-Part3 Certified Internal Auditor - Part 3, Business Analysis and Information Technology IIA-ACCA ACCA CIA Challenge IIA-CRMA Certification in Risk Management Assurance (CRMA) IIA-CIA-Part3-3P Business Knowledge for Internal Auditing IIA-CRMA-ADV Certification in Risk Management Assurance (CRMA Advanced) | ||||||||
| killexams.com IIA-CIA-Part3 exam PDF contains Complete Pool of Dumps and Dumps checked and Tested including references and explanations (where applicable). Our target to assemble the Dumps is not only to pass the exam at first attempt but Really Excellerate Your Knowledge about the IIA-CIA-Part3 exam topics. | ||||||||
| IIA IIA-CIA-Part3 Certified Internal Auditor - Part 3, Business Analysis and Information Technology https://killexams.com/pass4sure/exam-detail/IIA-CIA-Part3 Question: 414 The bullwhip, or whiplash, effect on inventories begins when retailers face uncertain demand from consumers caused by randomness in buying habits. It can be avoided by: A. The need to purchase or manufacture goods in cost-efficient batches. B. Changes in price that may encourage purchases in anticipation of future increases. C. Shortages that may lead to rationing by suppliers or manufacturers and hoarding by manufacturers or retailers. D. Sharing of information and coordination among the organizations in the supply chain. Answer: D Explanation: Sharing information about sales, inventory, pricing, advertising campaigns, and sales forecasts by all functions and organizations in the supply chain moderates demand uncertainty for all parties. The desired results are (1) minimization of inventories held by suppliers, manufacturers, and retailers; (2) avoidance of stockouts; (3) fewer rush orders; and (4) production as needed by retailers. Question: 415 A desired result of the sharing of information by all functions and organizations in the supply chain is: A. Fewer rush orders. B. Maximization of inventories held by suppliers, manufacturers, and retailers. C. Stockouts. D. Incompatibility of the information systems of the parties. Answer: A Explanation: Sharing information about sales, inventory, pricing, advertising campaigns, and sales forecasts by all functions and organizations in the supply chain moderates demand uncertainty for all parties. The desired results are (1) minimization of inventories held by suppliers, manufacturers, and retailers; (2) avoidance of stockouts; (3) fewer rush orders; and (4) production as needed by retailers. Question: 416 Which of the following are intermediaries between sellers and buyers? I. Agent II. Broker III. Consignee IV. Consumer A. I and II only. B. I and III only. C. I, II, and III only. D. I. II, III,and IV. Answer: C Explanation: A distribution channel is a series of interdependent marketing institutions that facilitate the transfer of a product from producer (seller) to consumer (buyer). Intermediaries include merchant middlemen, agents, brokers, consignees, and facilitating intermediaries. Question: 417 The channel structure in which producers, wholesalers, and retailers act as a unified system is a: A. Horizontal distribution system. B. Vertical distribution system. C. Unilateral distribution system. D. Multichannel system. Answer: B Explanation: In vertical distribution systems, producers, wholesalers, and retailers act as a unified system. Channel conflict is managed through common ownership, contractual relationships, or administration by one or a few dominant channel members. Horizontal distribution systems consist of two or more companies at one level of the channel working together to exploit new opportunities, such as the introduction of ATMs in supermarkets. The joint nature of horizontal distribution efforts is the tool for managing channel conflict. In a multichannel system, a single firm sets up two or more channels to reach one or more customer segments. Because such a system is managed by a single firm, channel conflicts can be evaluated and managed internally. Question: 418 Which of the following channel structures have the best means of managing channel conflict? I. Conventional II. Vertical III. Horizontal IV. Multichannel A. I and II. B. II, III,and IV. C. I, III,and IV. D. II and III. Answer: B Explanation: In vertical distribution systems, channel conflict is managed through common ownership, contractual relationships, or administration by one or a few dominant channel members. The joint nature of horizontal distribution efforts is the tool for managing channel conflict. In a multichannel system, because such a system is managed by a single entity, channel conflicts can be evaluated and managed internally. Conventional distribution systems consist of one or more independent producers, wholesalers, and retailers, each of which is a separate profit-maximizing business. The profit objective of each independent channel member may result in actions that are not profitmaximizing for the system as a whole, and the conventional distribution system offers no means for controlling channel conflict. Question: 419 The airlines have been leaders in the use of technology. Customers can make reservations either with an airline or through a travel agency. In this situation, a travel agency is classified as which type of distribution channel? A. An intermediary B. A jobber C. A distributor D. A facilitating agent Answer: A Explanation: Marketing intermediaries assist companies in promoting, selling, and distributing theirgoods and services to ultimate consumers. For example, travel agents access an airline's computerizedreservation system and make reservations for their customers without ever taking title to the ticket. Question: 420 On January 1, an entity issued a 10-year US $500,000 bond at 96% of its face amount. The bond bears interest at 12%, payable on January 1 and July 1. The entry to record the issuance of the bond on January 1 is: A. Option A B. Option B C. Option C D. Option D Answer: C Explanation: The entity received US $480,000 cash on the issuance of the bond. Its face amount is US$500,000, the amount to be paid at maturity. Hence, the credit to bonds payable is US$500,000. The US$20,000 difference is recorded as a discount on bonds payablea debitand is amortized over the life of the issue. For More exams visit https://killexams.com/vendors-exam-list Kill your exam at First Attempt....Guaranteed! | ||||||||
|
Data Protection 101 As threats continue to mount against customer networks, effective approaches to data protection are crucial for ensuring the integrity of stored information. In the event that antivirus, e-mail archiving or other security tools are compromised, or if a system crashes, having reliable backups and a strong disaster recovery plan in place can be a critical difference maker. There are several approaches and technologies that solution providers can leverage with their offerings to contribute to effective data protection. With a little help from CRN's Channel Encyclopedia, we'll examine various data protection methods, including different backup types, disaster recovery plans and data deduplication.
Backup Types Data backups are a critical part of the data protection and recovery process. Backing up data enables duplicate copies of data to be stored separately from the primary storage medium and ensures that data is available if the primary storage fails. When it comes to backing up files in a local data repository, there are different data backup types that serve different purposes. A full backup backs up all of the files in a repository. A differential backup allows the backing up of selected files. An incremental backup backs up files that were changed since the last full backup was done. A delta backup backs up data that has been changed in a file, and not the entire file itself. There are also several service providers that offer hosted, online backups. Storing data off-site through an online backup service or the cloud can be essential to a disaster recovery plan.
Disk And Tape Backup Backups can be performed on both tape and disk media. Tape backups involve using magnetic tapes to store duplicate copies of data separate from the primary storage medium. Magnetic tape can also be used to move and back up data from one storage array to another. While the restore process for tape backups can be complex, tape is much less expensive than disk. Disk-based backups aim to reduce backup management complexities by enabling fewer read errors and faster access to data, but are more expensive. Therefore it is common to see storage environments where backups are first done to disk for fast backups and restores, and then to tape for long-term and offsite archiving.
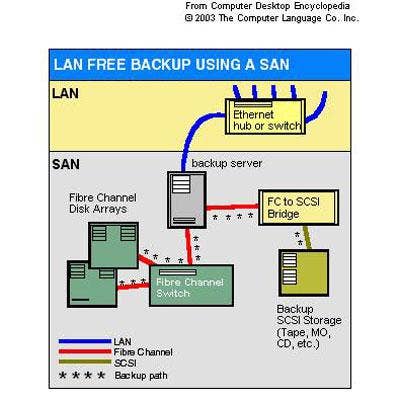
LAN Free Backup LAN free backup enables data to be backed up without transferring it over the LAN or WAN. LAN free backups can be accomplished with either a separate backup server or with a storage-area network (SAN) in place of a server. With backup servers, those devices handle the backups separately from the normal LAN traffic of customers' primary servers. A SAN, on the other hand, requires a separate network, typically configured with Fibre Channel, set up specifically for centralizing the storage and management of data.
Data Deduplication Deduplication removes duplicate information as data is stored, backed up or archived. It can be done at the file level, where duplicates are replaced with a marker pointing to a copy of the file, and/or at the sub-file or byte level, where duplicates are removed and replaced by pointers, resulting in a significant decrease in storage capacity requirements. Dedupe products can be classified in several ways. The first is according to where the dedupe takes place. Source dedupe dedupes the data before it is sent across a LAN or WAN. This results in fewer files and less data sent over the network, but affects backup performance because of the processing overhead. However, with new high-performance processors, this is less of an issue. Target dedupe starts the dedupe after the data is copied onto a destination device such as a virtual tape library. This takes away any overhead related to source dedupe, but requires more capacity at the target to temporarily store the entire data set.
Data Deduplication...Continued The second type of data deduplication occurs according to when the dedupe process occurs. With in-line dedupe, files are deduped as they are stored on a device. This adds processing overhead to the dedupe process, but does not require extra storage capacity for the dedupe process. With post-process technology, data is sent to the target device to be deduped. This requires extra capacity to temporarily store the incoming files before they are deduped, but takes the overhead away from the originating storage device.
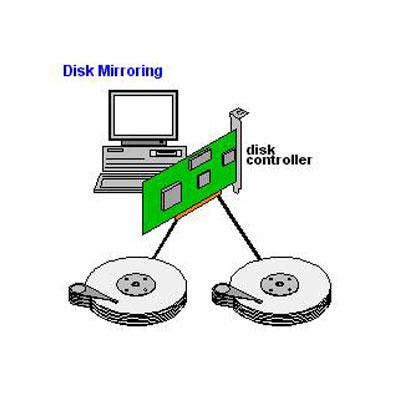
Disk Mirroring And Storage Replication Disk mirroring, also known as RAID 1 in a RAID array, is the process of recording multiple copies of data for a fault-tolerant operation to ensure data remains available if one copy is lost or corrupted. Disk mirroring can be done by writing the data on separate partitions of the same disk or on separate disks within the same system. Storage replication is similar to data mirroring, except that the second and subsequent copies of a data set are done over long distances, typically to a remote location.
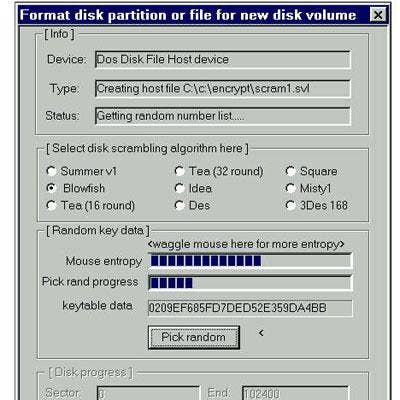
The Encryption Algorithm Cryptography refers to the conversion of data into scrambled code before it is transmitted over a public or private network using an encryption algorithm. The encryption algorithm uses a string of bits known as a "key" to perform the calculations needed to transform the data into a new form which cannot be read without the use of that key. For protecting data in transition, encryption is critical for ensuring confidentiality, integrity and in some cases even authenticity.
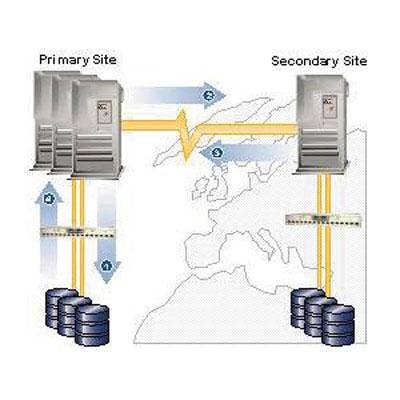
Disaster Recovery Planning A disaster recovery plan is exactly what it sounds like: a plan for duplicating all IT operations in the event of a disaster, such as a fire or flood. Disaster recovery planning ensuring that backed-up data as well as procedures for activating business-critical systems are available in a location located some distance from a user's primary data center. A key element to a disaster recovery plan is testing. Ensuring that backup systems and recovery methods will actually seamlessly restore day-to-day business operations and make the data accessible to all customers and employees is critical. In addition to the multiple service providers hosting disaster recovery services, there are various cloud computing platforms that also provide disaster recovery capabilities. (MENAFN- The Peninsula) The Peninsula Doha, Qatar: The Institute of Internal Auditors Qatar Chapter conducted training on 'Emerging Enterprise Risks with Evolving and Effective Control' by Tejjashree Rao, Chief Internal Auditor of British American Tobacco, UK, Middle East and Africa Regional Operations and Global Technology. The session focused on three areas: Emerging Risks Landscape, Controls and effective management of emerging risks. Tejjashree mentioned the Emerging risks landscape as“The perfect storm of high-impact interlocking risks faced by organizations.” Top risks were listed as macroeconomic and geopolitical uncertainty, Digital Transformation, Cyber and data security, Human capital and talent management, and ESG. “The emerging risks to move from reactive (measure & manage) to proactive (sense and respond) risk management. Predictive risk identification requires techniques like Horizon Scanning and Key Risk Indicators (KRI), Continuous monitoring, and Data analytics for audit risk assessments. Dynamic Risk Prioritization involves using risk velocity to gauge which emerging risks need immediate attention and warrant an audit. Adaptive Risk Response uses Agile Audit Principles to refine the design of controls as the risk evolves,” Tejjashree explained. Macroeconomic and geopolitical uncertainty risk-related controls that should be in place are scenario planning, liquidity management, financial modeling, and operational resilience. The consideration for audit is continuous monitoring with stakeholders. Digital transformation risk requires control by aligning project benefits to the organization's strategic goals and a robust program Governance, Oversight, and Status Reporting.“Internal audit should add more 'Advisory reviews' on the plan for key projects to provide real-time inputs as the project progresses through its lifecycle,” stated Shree as a solution. Cyber and Data Security risk mitigation controls consist of Cyber Incident Response and Recovery Plans, Identity and Access Management Policies and Standards, and Cyber threat intelligence and monitoring procedures. Internal audits should consider Automated Continuous Control Monitoring reports to provide a more real-time view of vulnerable areas. Human capital and talent management risk cannot be taken lightly by auditors. Conducting thematic culture audits covering identified hotspots and additional audit ratings for management risk awareness and control culture is recommended.“During all audits, evaluate how the Function/business area is mitigating People risks,” Shree enforced. The main aspects of ESG risks and controls are to monitor progress made against ESG goals and regulatory requirements from international laws on ESG. Focus is to be given to ESG Data Management, especially on those metrics that are externally reported. “The training imparted invaluable insights into emerging risks, effective internal control, and internal audit preparedness. Shree emphasized auditors deliver value through planned assurance and continuous controls monitoring, insights & foresight through increased automation & data analytics, and an improved organizational risk & control culture. The perspectives provided were compelling, relatable, and adaptable,” Sundaresan Rajeswar, Board Member, said in his concluding remarks. Girish Jain, seminar chair, conducted the Question and Answers session and opened the meeting. Robert Abboud, Past President of the IIA, spoke during the closing session. MENAFN18122023000063011010ID1107616121 Legal Disclaimer:
Geographic Information Systems (GIS) represent a revolution in the way spatial data can be captured, processed, analyzed, displayed, and stored for future retrieval. Maps have always been an essential tool for planners and decision-makers, and GIS have greatly enhanced the ability to process and make easily accessible all types of geographic information By linking GIS to relational databases, for example, large sets of data can be made accessible to analysis and retrieval, allowing for the inclusion of comprehensive natural resource and socioeconomic information for planning and decision-making for sustainable development. Two technologies related to GIS are remote sensing and global positioning systems (GPS). Remote sensing techniques allow for the compilation of extraordinarily detailed images of the Earth's surface through satellite imaging, with which of up-to-date inventories of urban sprawl, natural disasters such as forest fires and floods, assessments of vegetation vigor, and of many other natural resources data can be produced. GPS are very precise instruments for locating exact coordinates on the Earth's surface, which they do by studying satellite signals. The information generated by both of these technologies can then be incorporated and processed using GIS. A GIS can be an important component of a decision-support system (as is the case for ALES or CRIS), or in fact can constitute a decision-support system on its own, as it can allow for modeling of different scenarios, and the integration of several layers of information with stakeholder requirements. A GIS allows for the essential functions of geographical analysis to be exercised and related to decision support requirements for management. Managers can use this to build models of systems and then use the models to assess the impact of each of a series of potential decisions. GIS technology can help establish cross-sectoral communication - by providing not only very powerful tools for storage and analysis of multisectoral spatial and statistical data, but also by integrating databases of different sectors in the same format, structure and map projection in the GIS system. With information that records the location of many different properties of the earth, it becomes possible, to use a GIS to relate vegetation cover to infrastructure. In land use planning, for example, a GIS can be used to find the location of vegetation types of commercial or conservation interest to be left intact, and to suggest alternative areas suitable for developing housing with minimal ecological impact, and maximal protection from natural hazards such as floods, forest fires, etc. A GIS can be useful both for solving emergency situations created by fire or flood, or for longer-term planning based on the comparison of the distribution of natural resources at different dates, which allows for the estimation of rates of change or consumption. GIS has become a cost-accessible technology (for example, free GIS software is available over the internet), and the collective experience of developed and developing countries in setting up and using GIS has become a reliable asset for making good decisions in choosing strategies for implementing these systems in the Caribbean SIDS. One of the main information management concerns for Caribbean SIDS is the standardization of data collection and software systems. In many instances, the type of software that has been used in the past has been decided on a project-specific basis by the international agency that implemented the project. There has been no national policy on standards in GIS utilization. This has resulted in a fragmentation of data and system types, impeding the integration of data into larger datasets and the universal access to coverage data. GIS expertise is another challenge. Caribbean governments do not have enough people with GIS expertise to develop effective systems. Evidently, the training and development of awareness about GIS and its potential amongst government officials is paramount. A study done in 1998 under the Caribbean Planning for Climate Change (CPACC) Project (Review of GIS Capability and Needs in CPACC Partner Institutions) concluded that the countries under the program had several commonalties in terms of GIS equipment and strategies of development, with differences at the level of advancement. Thus, countries with relatively advanced GIS capacity and coastal databases included Barbados, Belize, Jamaica, and Trinidad and Tobago; countries with functional GIS but little coastal GIS databases included the Bahamas, Dominica, Guyana, Saint Lucia, and St. Vincent and the Grenadines; countries with GIS equipment but limited GIS databases or expertise include Antigua & Barbuda, Grenada, and St. Kitts & Nevis. Recently, governments in the region have placed emphasis on the use of GIS, particularly for land use planning purposes, and have established GIS units within several critical ministries. An example of this is Jamaica's National Environmental and Planning Agency (NEPA), which ranks as one of the most advanced institutions in the region in terms of GIS capacity. Ideally, GIS systems and data would be standardized across the region, interlinked, and made accesible through the internet for the sharing of geographical information. Links to sites relevant to GIS and sustainable development CDMP Natural Hazard Mapping Resources Page CHAMP Inventory of Hazard and Vulnerability Assessment Maps and Data Data Collection and Automation in GIS Workshop Food and Agriculture Organization of the United Nations (FAO) GIS and Sustainable Development GeoCaribe PROCIG - Central American Geographic Information Project Use of GIS and Remote Sensing Techniques in the Sustainable Agricultural Management and Development. The Indian Experience. The Draft Proceedings of the Regional Training Workshop on Methodologies for Coastal Inventories & Information Management. (MENAFN- ForPressRelease) Accreditationconsultancy is delighted to launch the ISO 17020 Accreditation e-learning courses. The E-learning courses like the ISO/IEC 17020 Awareness training course, ISO/IEC 17020 lead auditor training, and ISO/IEC 17020 certified auditor training course- are designed to give training and certification for anyone interested in becoming ISO 17020 auditors for Quality Management Systems in inspection agencies. ISO 17020 E-learning courses are mostly useful for people who want to join the e-learning course from the comfort of their own home or office at their own pace. The ISO/IEC 17020 internal auditor training course is an online course that provides Quality Management System auditors at inspection agencies with training and certification. The course covers audit techniques, processes, and requirements, allowing firm workers and inspection organization auditors to become certified internal auditors for ISO/IEC 17020:2012. The ISO/IEC 17020 lead auditor training course covers the ISO/IEC 17020:2012 Accreditation for Inspection Bodies requirements, including an overview of the standard, general requirements, and the goal of ISO 17020:2012 standards. The courses include real-world and practical examples, and participants will get an ISO/IEC 17020 Lead Auditor certificate that can be confirmed at any time. The training courses also assist steadfast personnel and inspection agency auditors in becoming a 'Certified Internal Auditor' by the ISO/IEC 17020:2012 standard standards. The ISO 17020 lead auditor, ISO 17020 Awareness training, and ISO 17020 certified auditor training E-learning courses include interactive online sessions that include lectures, audio-visual presentations, handouts, and online examinations to ensure a complete understanding of the subject. These courses guide us: The documentation required for the implementation and ISO/IEC 17020 accreditation, steps for ISO /IEC 17020 accreditation, use of ISO 17020 audit checklist, ISO 17020 clauses, list of procedures and records, PDCA cycle, types of auditing, how to prepare internal record, organizational issues, risk management and risk assessment techniques. The ISO 17020 auditor training online courses are intended for professionals, QA Assessors, Quality Managers and other individuals, college students, and people looking to advance in their careers. It enables individuals to compete in today's competitive climate by allowing them to renew licensees and upgrade their knowledge and abilities. The training is also beneficial for people pursuing certification or beginning a new career. The ISO 17020 awareness online course is appropriate for inspection body personnel and managers, as well as ISO 17020 consultants. The courses were developed by a team of ISO consultants with over 25 years of ISO and management consulting expertise in over 35 countries. The course is created and delivered efficiently and cost-effective manner, making it ideal for individuals seeking to become ISO/IEC 17020:2012 Certified Internal Auditors. About Accredtationconsultancy Company :-Accreditationconsultancy User :- accreditation consultancy Email :... Phone :-7929795322 Url :-MENAFN28122023003198003206ID1107665162 Legal Disclaimer: Barrons Roundtable panelists discuss how you can adjust your 2023 portfolio for success in 2024. The Internal Revenue Service (IRS) is warning taxpayers and tax professionals to be on the lookout for emerging scams and protect sensitive information as the filing season approaches. The IRS released the warning to taxpayers as it observed National Tax Security Awareness Week in concert with its Security Summit partners. The Security Summit includes 42 state tax agencies as well as other entities connected to the tax community – including tax preparation firms, software developers, payroll and tax financial processors, tax professional organizations and financial institutions. Tax filing season is expected to begin in mid-January 2024. "Identity thieves are relentless and use a variety of techniques," said IRS Commissioner Danny Werfel, who added that he would "urge people to be careful with their personal information and be wary of email and text scams." "With people anxious to receive the latest information about a refund or other issues during tax season, scammers will regularly pose as the IRS, a state tax agency or others in the tax industry. People should be incredibly wary about unexpected messages that can be an elaborate trap by scam artists, especially during filing season," Werfel added. IRS MOVE COULD CARRY HEFTY COST FOR SOME TAXPAYERS The IRS, state tax agencies and other entities in the tax community are warning taxpayers about scams ahead of tax filing season. (Photographer: Timothy Fadek/Bloomberg via Getty Images / Getty Images) The IRS noted that identity thieves will also use latest news events and tragedies as part of an effort to trick taxpayers. Another common tax season scam involves identity thieves contacting tax professionals posing as new, potential clients by email or phone to access a company’s systems that could enable them to file fake tax returns to secure a refund. IRS’ VENMO CRACKDOWN DELAYED BUT NOT DEAD THIS HOLIDAY SEASON IRS Commissioner Danny Werfel warned, "People should be incredibly wary about unexpected messages that can be an elaborate trap by scam artists, especially during filing season." ((Tom Williams/CQ-Roll Call, Inc via Getty Images) / Getty Images) Taxpayers should be on alert for phishing emails sent by fraudsters claiming to come from the IRS or another legitimate entity like a state tax organization or financial firm that looks to lure unsuspecting victims with the promise of a phony tax refund or false allegations of tax fraud. Similarly, "smishing" messages sent via text message have emerged as a similar technique and may claim a taxpayer’s account has been put on hold or send a fake unusual activity report with "solutions" to restore the recipient’s account. Individuals "should never respond to tax-related phishing or smishing or click on the URL link," the IRS noted. "Instead, the scams should be reported by sending the email or a copy of the text/SMS as an attachment to phishing@irs.gov." Unexpected emails or text messages purporting to be from the IRS or other official tax community sources could be from fraudsters and contain malware or ransomware. (iStock / iStock) GET FOX BUSINESS ON THE GO BY CLICKING HERE The IRS notes that it initiates most contacts through regular mail, so taxpayers shouldn’t be getting an unexpected message by email, text or social media about a bill or tax refund. Partners in the IRS Security Summit also reminded taxpayers and others to never click on any unsolicited communication that claims to be the IRS or another entity in the tax community because such links can surreptitiously load malware onto the device in use. It can also allow malicious hackers to load ransomware that prevents a device owner from accessing their system or file. CFO at Avanade, overseeing global investment strategy, accounting, budgeting, tax, internal audit, financial planning and treasury. Getty Give me a multitab spreadsheet thick with numbers, and I will gleefully dig into it as if it were a summer blockbuster novel. Bizarrely, however, not all business leaders share my fascination with the deep intricacies of financial analysis. Over the course of my career, one of the most valuable lessons I have learned is the value of storytelling and how to use stories to convey financial information. Whether on a Microsoft Teams or video call or, hopefully again soon, presenting in person, as finance leaders, we can employ storytelling techniques to present financial information in a compelling and memorable way. Here are some tips I share with my team: Incorporate storytelling basics into your presentations. Executives have so much information thrown at them and so little time. To make an impact, determine the two or three points you want your audience to home in on, and build your presentation from there. Most of us have learned this the hard way, but it is worth repeating: The worst mistake you can make is studying what is on your presentation deck. People can read faster than you can speak. If you give too much to read, they won’t listen to you. The antidote to the dreaded “spreadsheet pasted onto a slide” is visuals. Personally, I’m a big fan of illustrations and images, and I use them as often as I can. My team and I spend a bit of time thinking how best we can present financial data as a visual. While we can’t get away from numbers completely, we use them as sparingly as possible and make sure they are presented in a crisp, clean, uncomplicated format. Understandably, almost everyone walks into a presentation asking themselves, “Why do I need to know this?” If you don’t answer this “so what” question upfront, too often you’ll find your audience double-tasking or scrolling through their phones. I often set the stage, saying something like, “Understanding these numbers will allow us to determine what level of investment we can comfortably make in the coming quarter,” or whatever is appropriate to the situation. Avoid financial jargon and acronyms. Even when I am speaking to a financially astute audience, I know that the familiar financial terms I may use without thinking could cause confusion. My company is in professional services and technology — an already acronym-heavy industry. So it is even more important for certain fields. Better that everyone easily understands the point I am making. One of my most important lessons over the years has been the importance of practice. Practice your presentation multiple times. Then once you think you have it mastered, practice it again with a nonfinance person or two who may have no idea what you’re talking about. Are you presenting your material so clearly that they come away with an understanding of your main points? Were you able to hold their attention? Keep an eye on the energy of your audience. This is more challenging to do now that we are generally working remotely, but keep tabs on how your audience, whether it’s your leadership team, board of directors or shareholders, is reacting. We all know how hard it is to stay attentive and engaged. If you find yourself scheduled in the middle of a long day of presentations, do something to change the dynamic. One easy trick: Consciously vary your tone of voice. A monotone is deadly. Especially on conference calls, smile while you are speaking, when appropriate. You will be surprised how much more inviting you sound. If you are presenting an ask, such as a sales goal, and sense your audience is dubious about your ability to achieve it, break it down into steps. Then it feels possible. Another tactic is to translate a financial goal into a reference that is easily relatable. As a fictional example, say we want to grow 10% in a given time frame. I might say, “That’s equivalent to adding a country’s monthly revenue to our portfolio.” Hit bad news head-on. If there’s something that will be a red flag, bring it up first. In situations like that, I will often say, “You’re probably asking yourself…” and then be ready with an answer, approach or proposed solution. Years ago, a sales leader I know walked into a meeting wearing a football helmet. It broke the tension, reset the energy in the room and gave him the opening he needed to present the challenges his unit was facing — and then move on to his proposed solutions. With just as much style and even a bit of gallows humor, it’s equally important to develop a way to keep your cool if things go sideways, because let’s be honest: Not every presentation will go well. Don’t feel like you have to go it alone. While most of us did not study design as part of our finance curriculum, likely there are people in your company who did. At our company, I am fortunate to have access to a network of presentation and user experience professionals. When I am faced with an important presentation, I turn to them to help me create visually compelling materials. Consider consulting with your own company experts. Of course, in the end, it all comes back to numbers. As long as we help others understand what the data is telling us, as clearly and memorably as possible, we have equipped our audiences to make the best decisions possible. If you would like to learn more about how to incorporate storytelling into your presentations, a book I have found particularly helpful is Weekend Language: Presenting with More Stories and Less PowerPoint by Andy Craig and Dave Yewman. Forbes Finance Council is an invitation-only organization for executives in successful accounting, financial planning and wealth management firms. Do I qualify? UBS AG is committed to taking reasonable steps to provide protection for essential activities should any event disrupt normal business operations. UBS AG has developed a rigorous Business Continuity Management (BCM) program to maintain the highest standards of resiliency at all times during our daily practices. The BCM group is an integral part of UBS' normal business operations. UBS AG recognizes its responsibility to help protect global financial systems and, as such, meets regulatory guidelines and recommendations through a global, regional and structured approach. UBS AG’s BCM program considers various levels and types of disruptions that might affect a building, business district, city or a wide-scale condition within a region or multiple regions. A dedicated team of business continuity professionals ensure that recovery plans are documented, reviewed and tested. UBS AG is committed to ensuring that its BCM program is comprehensive and up-to-date, particularly as new information, techniques, and technologies become available. UBS AG actively engages with industry bodies to develop and enhance resiliency within the financial sector and partners closely with regulatory bodies to advance Business Continuity planning in all regions. Although we have taken significant steps to develop and implement sound business recovery plans, we cannot guarantee that systems will always be available or recoverable after a disaster or significant business disruption. However, we believe that our planning for such events is robust and consistent with many of the best practices established within the industry enabling an effective response that safeguards the interests of our key stakeholders, reputation, brand and value-creating activities. Employee confidentiality agreements are meant to prevent employees from disclosing confidential information about their employers. These agreements give employers assurance that their trade secrets, such as customer lists and business plans, are protected from their competitors. An employee's obligation to keep information confidential can last even after the employee has left the company. | ||||||||
IIA-CIA-Part3 exam Questions | IIA-CIA-Part3 tricks | IIA-CIA-Part3 study help | IIA-CIA-Part3 syllabus | IIA-CIA-Part3 information search | IIA-CIA-Part3 pdf | IIA-CIA-Part3 guide | IIA-CIA-Part3 test | IIA-CIA-Part3 benefits | IIA-CIA-Part3 PDF Download | | ||||||||
Killexams exam Simulator Killexams Questions and Answers Killexams Exams List Search Exams |